6.4: Exploitation tools (Pt 1)
Por um escritor misterioso
Descrição

PCI DSS Tackles Client-Side Attacks: Everything You Need to Know About Complying With PCI 6.4.3

WordPress 6.4: What's Coming in the Next Version
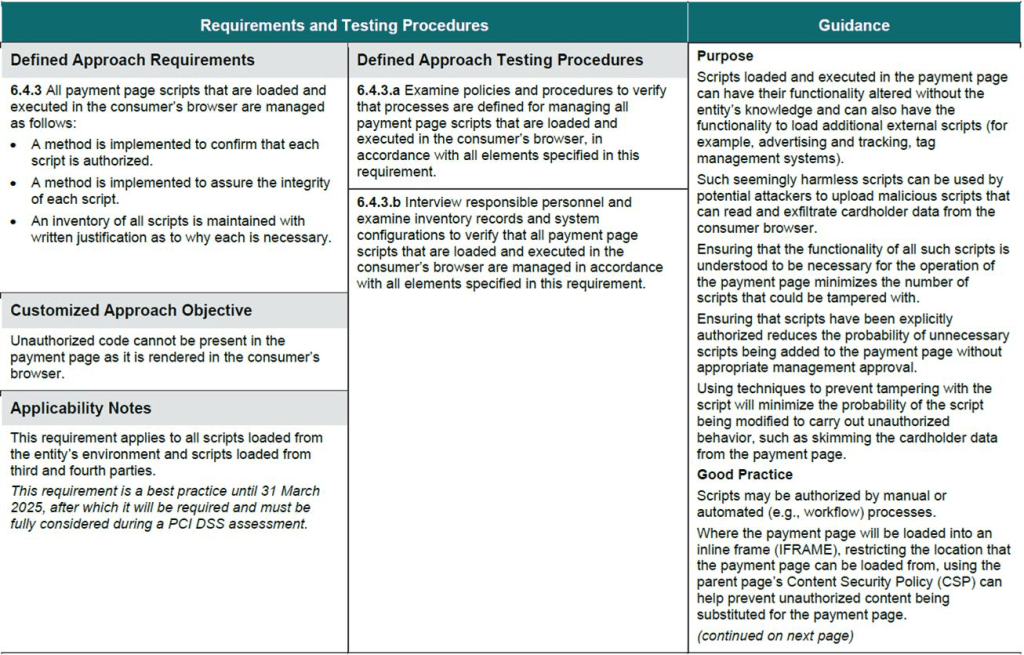
Understanding PCI DSS's New Client-side Security Requirements: Section 6.4.3
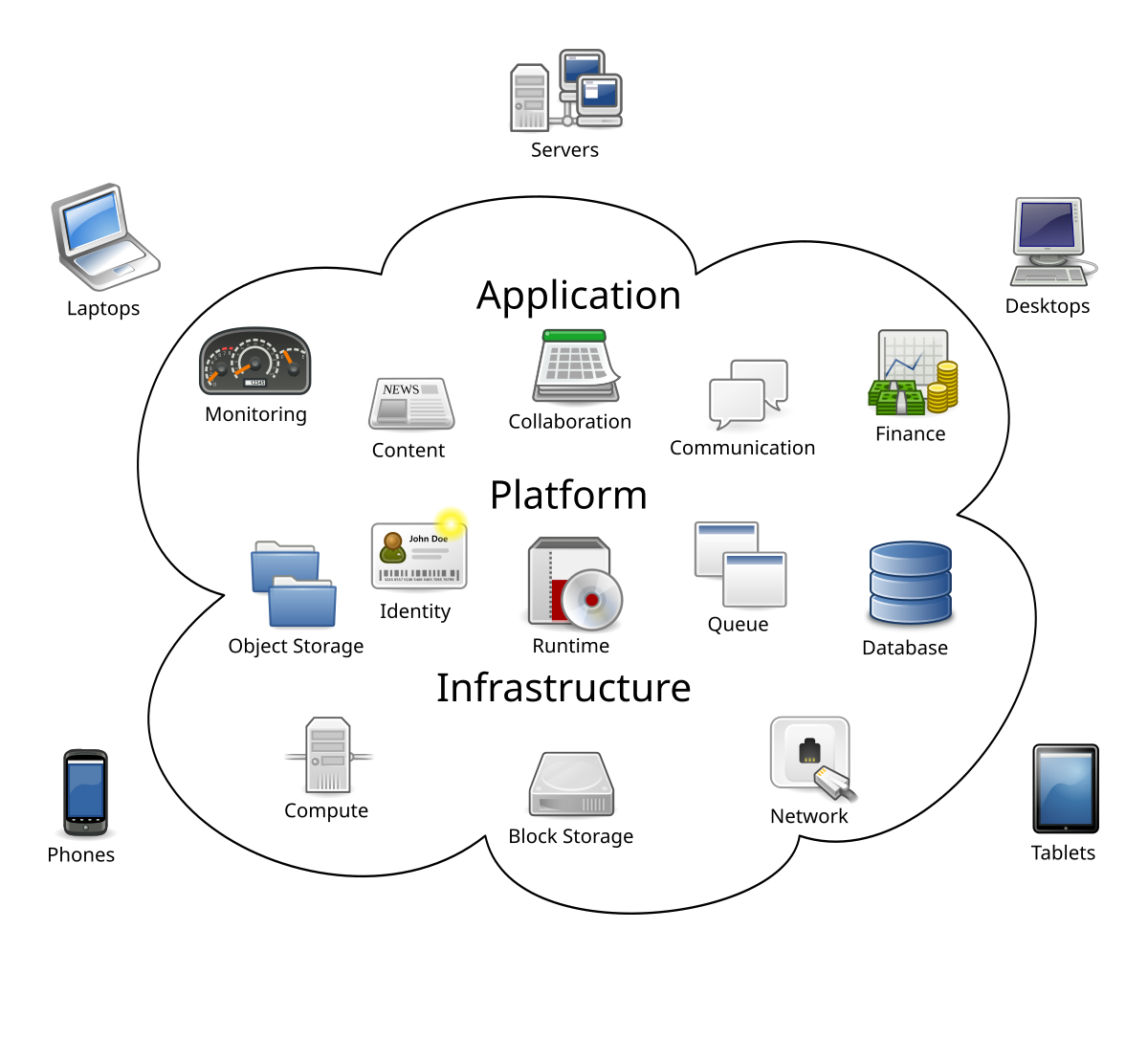
Cloud computing - Wikipedia

Physical water scarcity metrics for monitoring progress towards SDG target 6.4: An evaluation of indicator 6.4.2 “Level of water stress” - ScienceDirect

WordPress Critical Vulnerability Fixed in Patch 6.4.2 – Gridinsoft Blog

Advanced strategies to thwart foreign body response to implantable devices - Capuani - 2022 - Bioengineering & Translational Medicine - Wiley Online Library
ETL listed, patented, fused safety plug Pivots up and down for focused airflow Assembles easily with no tools needed Features storage compartment for

Lasko 2002W Personal Fan, 6-Inch, White, 2002
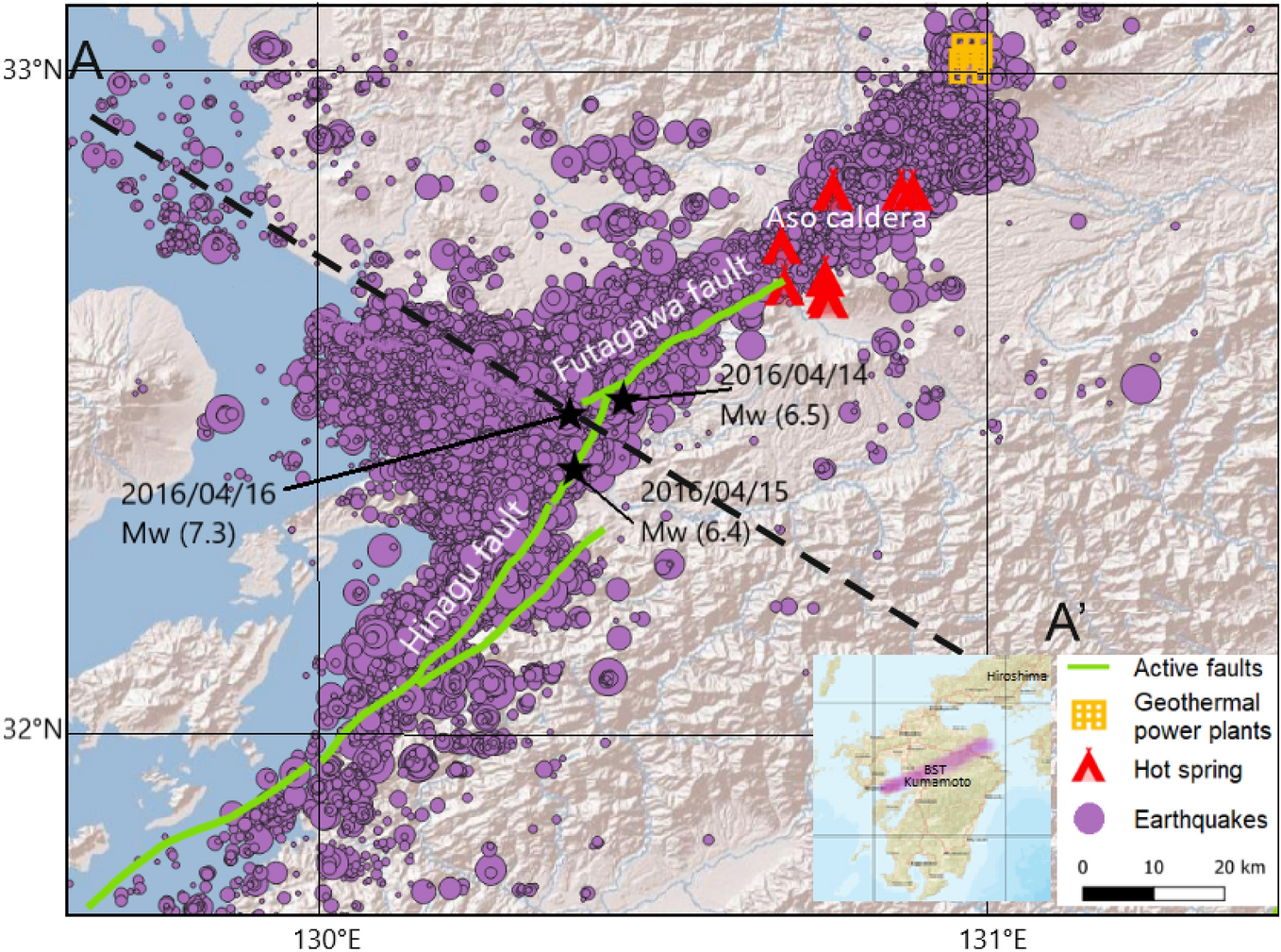
Dynamics between earthquakes, volcanic eruptions, and geothermal energy exploitation in Japan
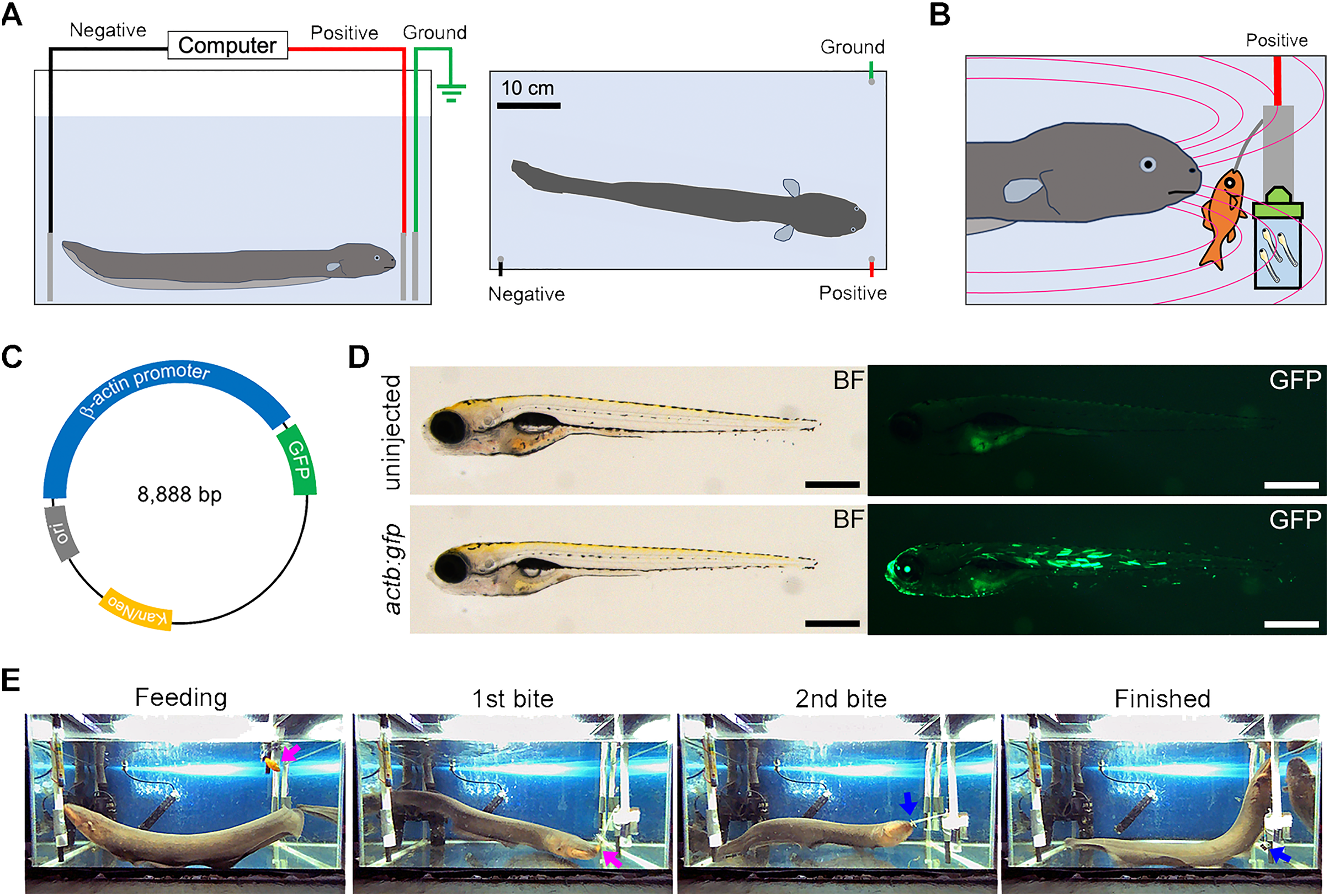
Electric organ discharge from electric eel facilitates DNA transformation into teleost larvae in laboratory conditions [PeerJ]

Exploiting AD - Part 1 [Active Directory Hacking] -- TryHackMe LIVE!

Center for Internet Security (CIS) Controls - TermsFeed

SDG indicator 6.4.1 “change in water use efficiency over time”: Methodological flaws and suggestions for improvement - ScienceDirect
de
por adulto (o preço varia de acordo com o tamanho do grupo)