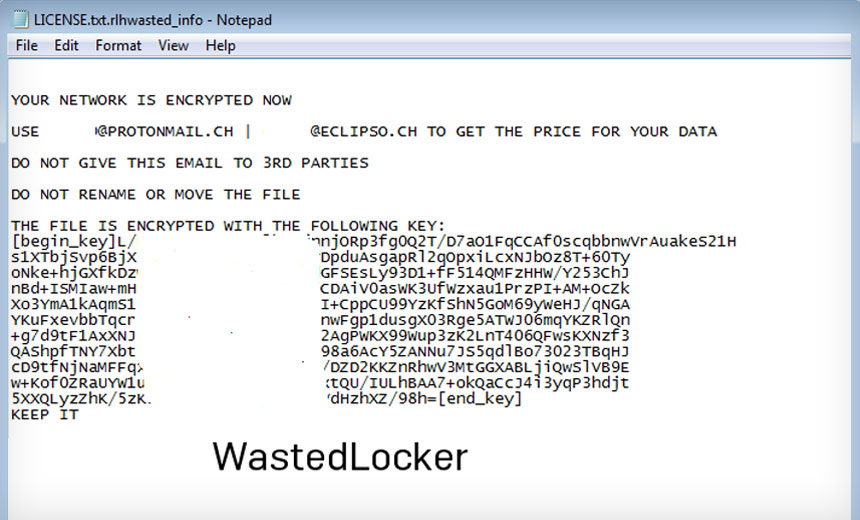
IoT Botnets: Advanced Evasion Tactics and Analysis – Part 2
Por um escritor misterioso
Descrição
Nozomi Networks Labs analyzes new modification techniques malware authors use to evade detection and analysis tools.

A Comprehensive Survey of Recent Internet Measurement Techniques for Cyber Security - ScienceDirect

IoT Botnets: Advanced Evasion Tactics and Analysis – Part 2

Worm-like propagation of Sysrv-hello crypto-jacking botnet: Network traffic analysis and latest TTPs
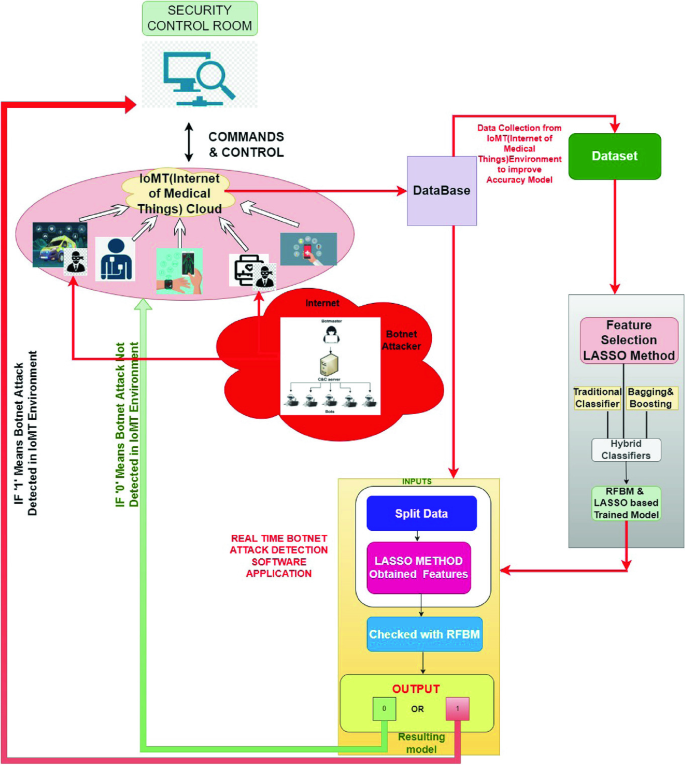
Botnet Attacks Detection Using Embedded Feature Selection Methods for Secure IOMT Environment
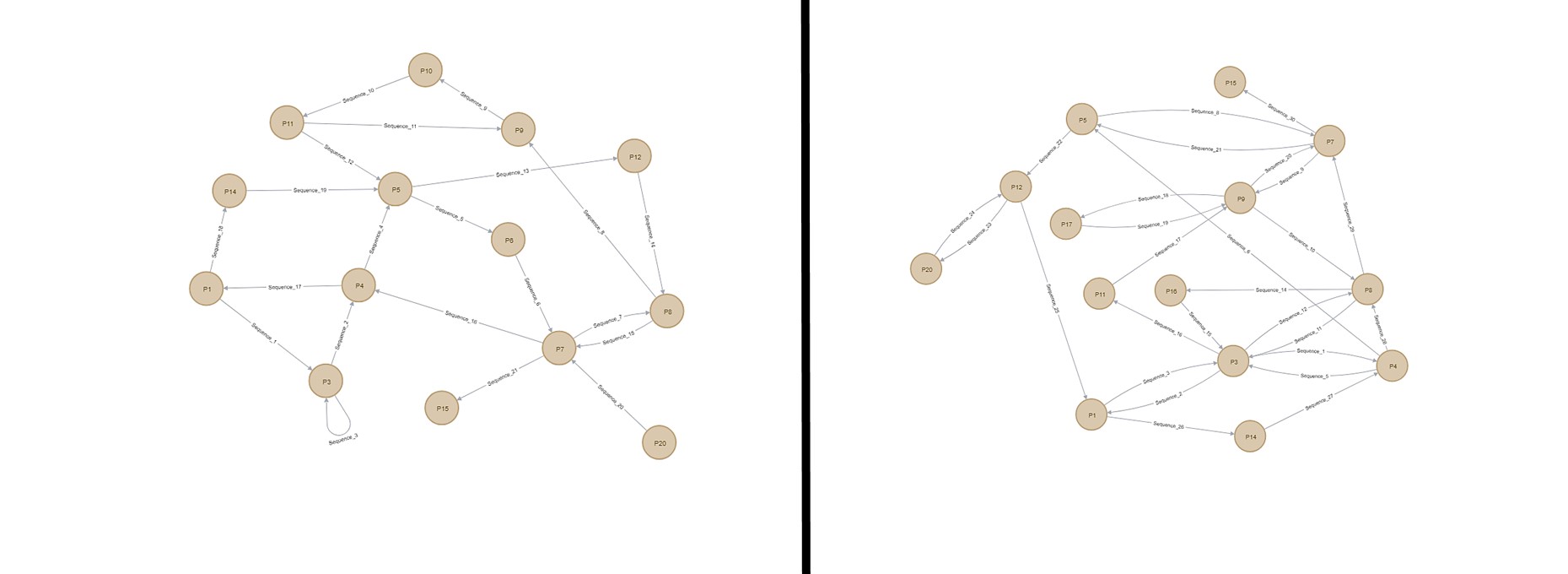
Identifying malicious IoT botnet activity using graph theory
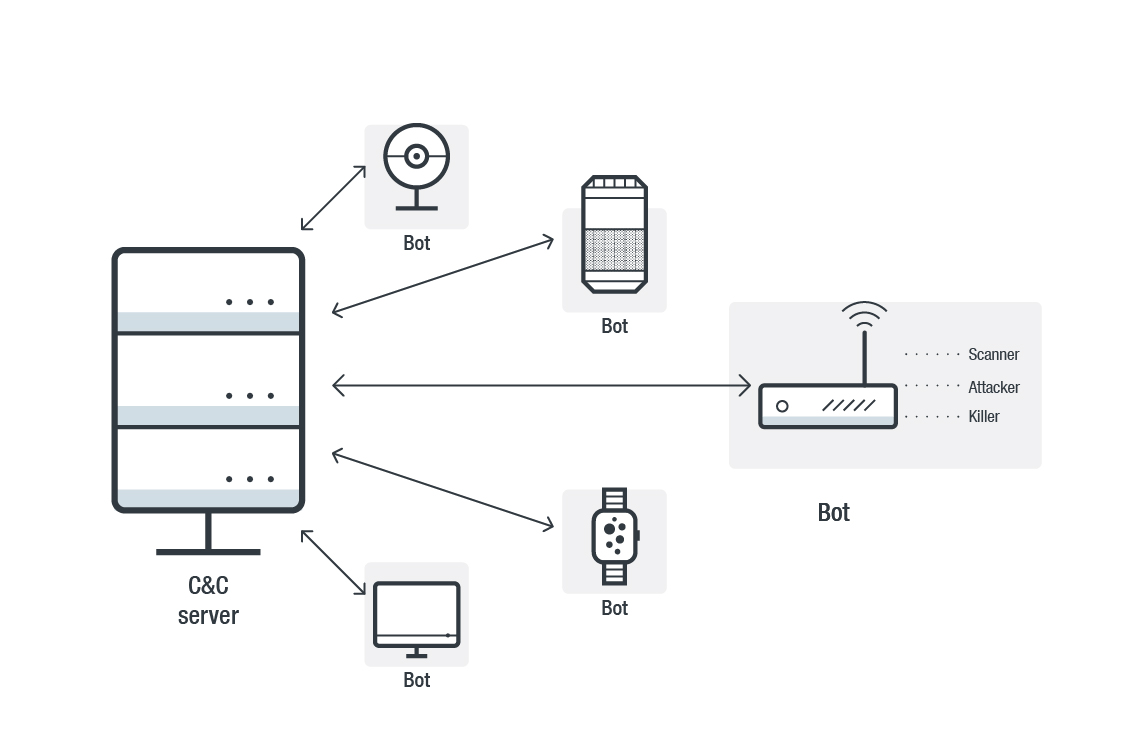
Into the Battlefield: A Security Guide to IoT Botnets - Security News

Jayson Pieterse posted on LinkedIn
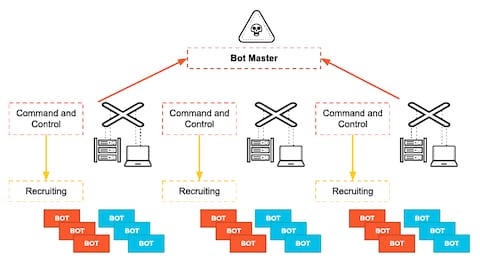
What is a Command and Control Attack? - Palo Alto Networks

Securing Internet of Things (IoT) with machine learning - Zeadally - 2020 - International Journal of Communication Systems - Wiley Online Library
Sensors, Free Full-Text

GoTrim botnet actively brute forces WordPress and OpenCart sites
de
por adulto (o preço varia de acordo com o tamanho do grupo)