Hack Attacks Testing How to Conduct Your - Back to Home
Por um escritor misterioso
Descrição
Hack Attacks Testing How to Conduct Your - Back to Home

Hack the 10 Steps of the Pentesting Routine - PlexTrac

Complete Guide to Ransomware: How to Recover and Prevent an Attack

Hack Attacks Testing: How to Conduct Your Own Security Audit: Computer Science Books @
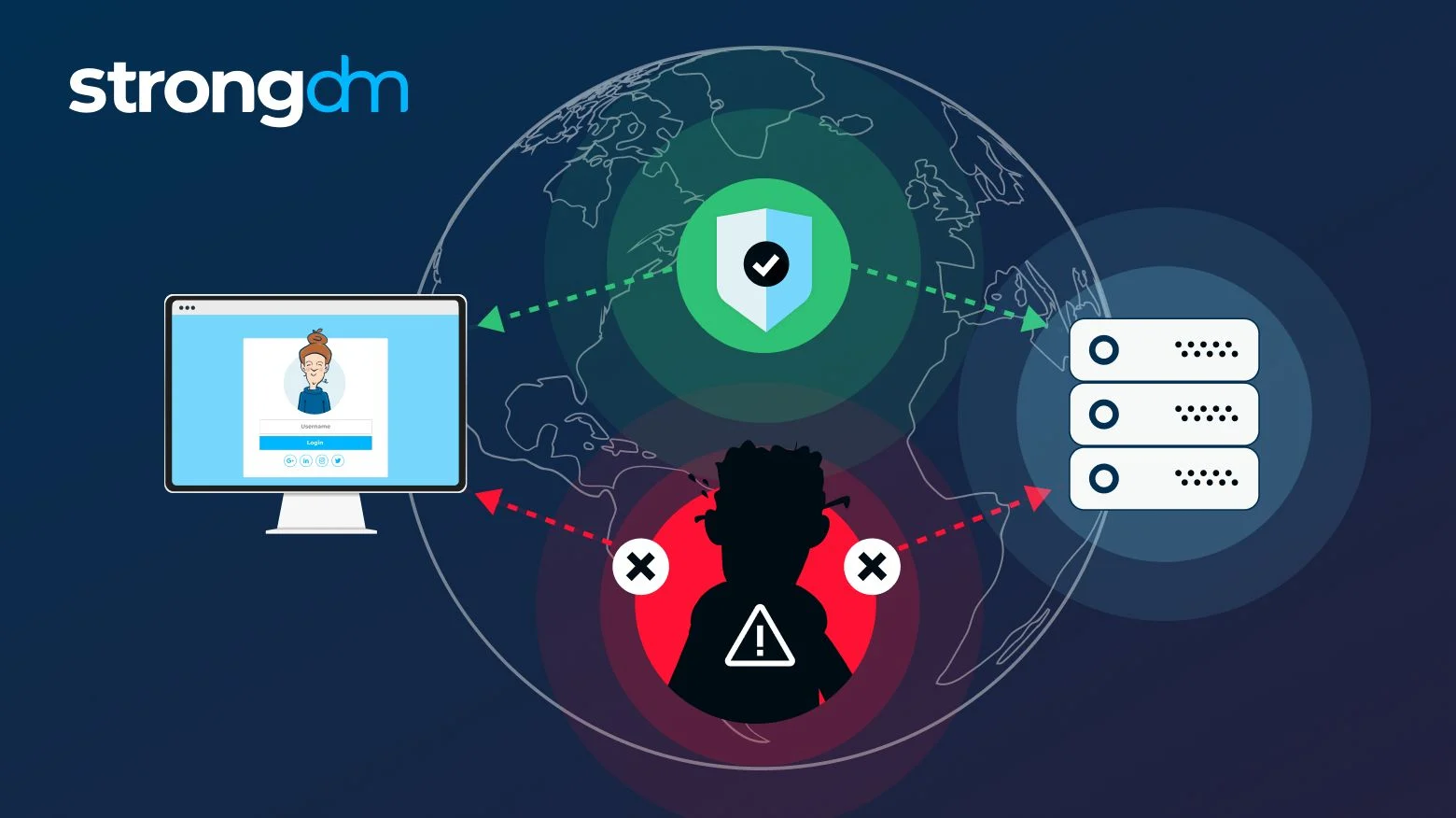
Man-in-the-Middle (MITM) Attack: Definition, Examples & More

The 27 Most Notorious Hacks History

How a smart home could be at risk from hackers - Which? News
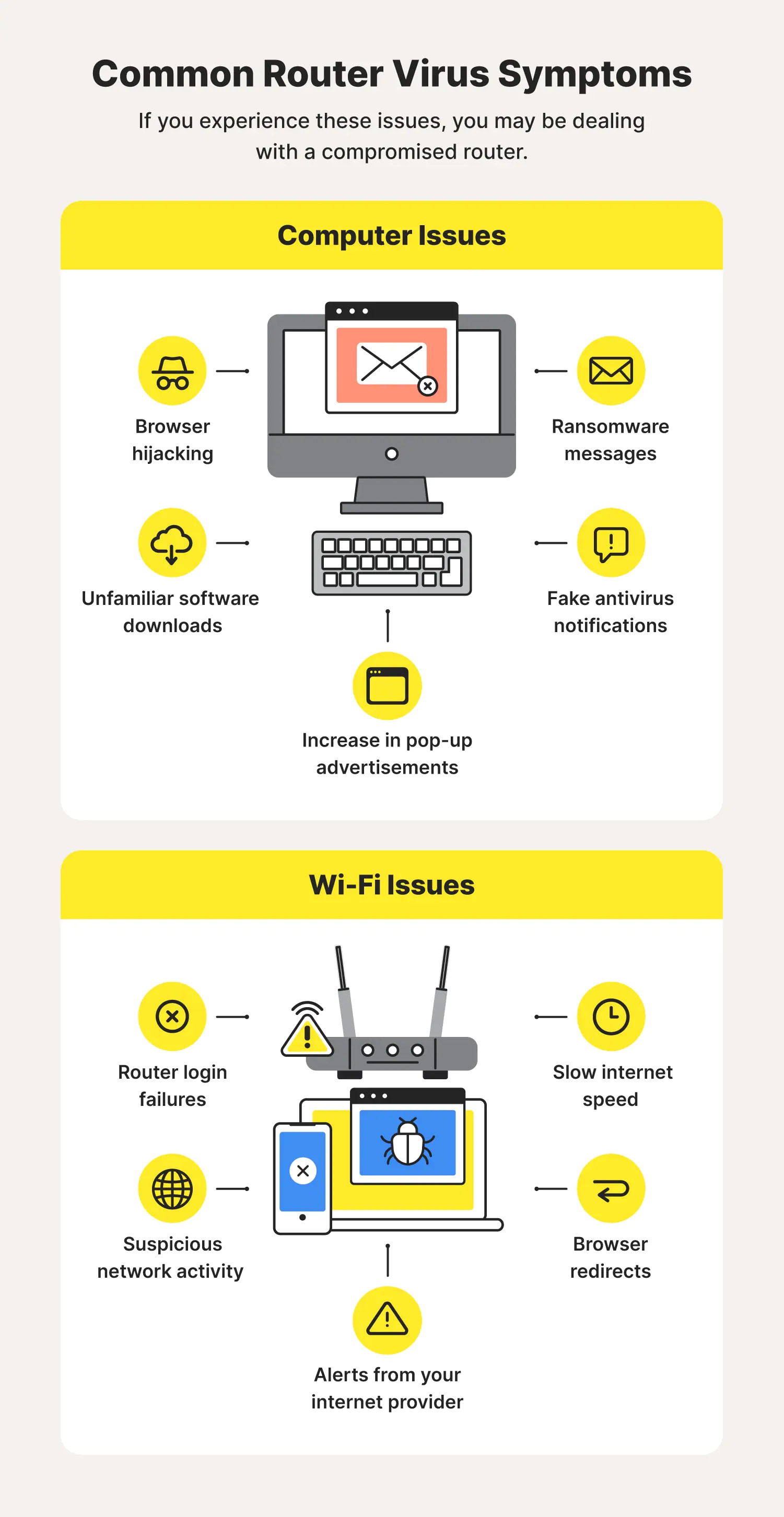
How to tell if someone hacked your router: 10 warning signs - Norton

Exclusive: Russian hackers targeted U.S. nuclear scientists

Would you know how to fix a hacked home device? Here's what to do!
List of Data Breaches and Cyber Attacks in 2023 - IT Governance UK Blog
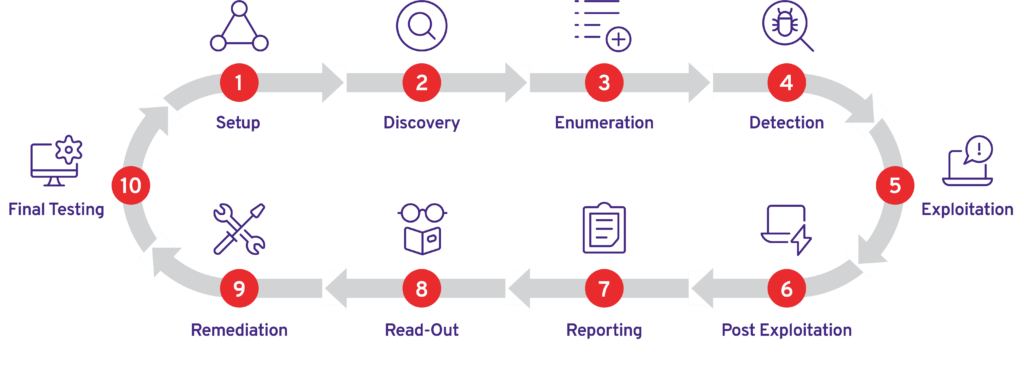
Hack the 10 Steps of the Pentesting Routine - PlexTrac

What you actually need to do if you're hacked - F-Secure Blog
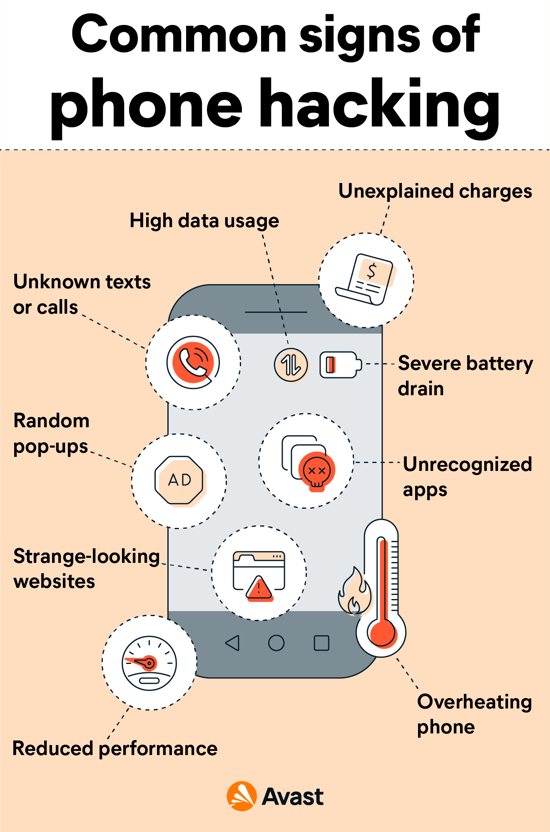
10 Signs That Your Phone Has Been Hacked

Hack The Box: Hacking Training For The Best

Penetration Testing: A Hands-On by Weidman, Georgia
de
por adulto (o preço varia de acordo com o tamanho do grupo)