Business Email Compromise and Defense
Por um escritor misterioso
Descrição
Email is critical to the lifeblood of modern business. Business email compromise (BEC) is no joke, and continues to increase despite increased awareness. The people behind these scams know how to trick users, relying on a variety of technical tools, urgency and fear to direct funds and steal sensitive information.

What is Business Email Compromise (BEC)? – Proofpoint Education
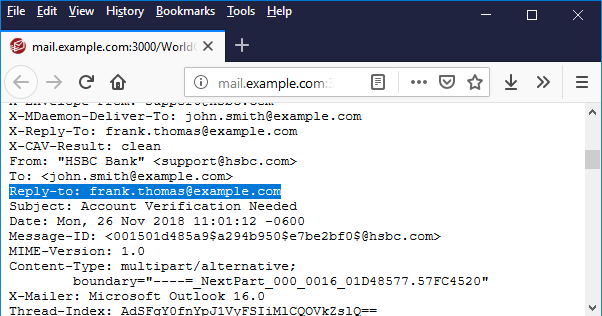
Best Practices to Avoid Business Email Compromise & CEO Fraud Attacks

Vendor Email Compromise: Stop Fake Invoices & Payment Diversion Scams

Business Email Compromise - Why Is It Dangerous and How to Avoid

Business Email Compromise (BEC) - Definition

What Is BEC? - Business Email Compromise Defined

Business Email Compromise Attacks in Many Ways
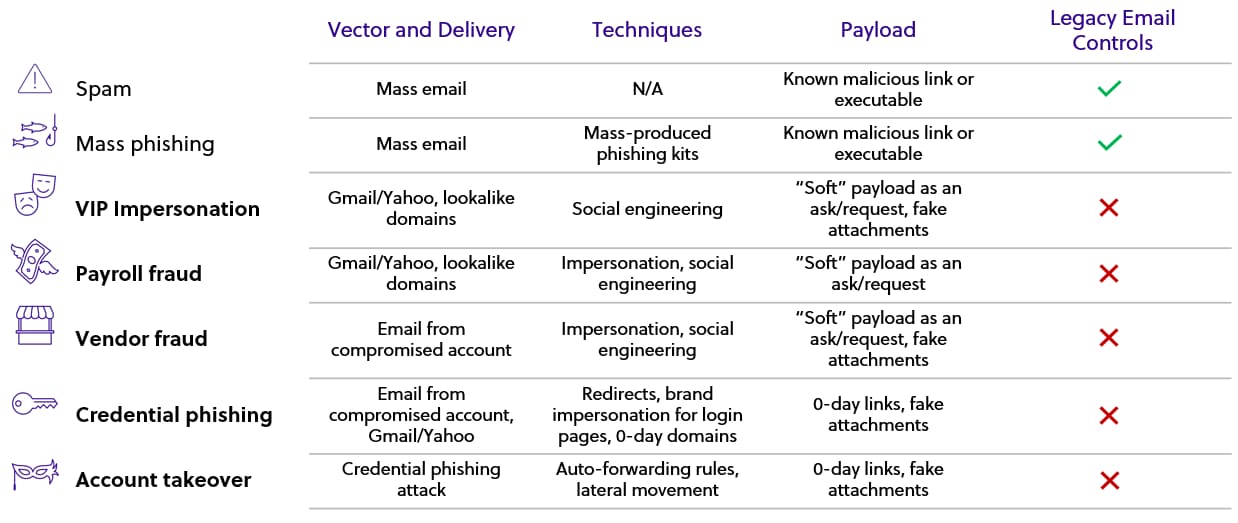
What Is Business Email Compromise (BEC)? - Cisco

Demystifying Business Email Compromise (BEC): Don't fall for the

Behind the scenes of business email compromise: Using cross-domain

Business Email Compromise and Defense

What is Business Email Compromise (BEC)?

Business Email Compromise (BEC) Phishing Protection
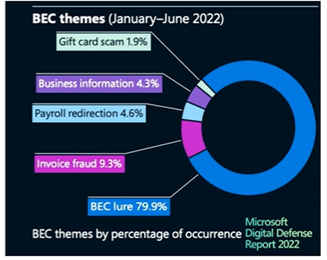
An Insider's Guide to Business Email Compromise Attack Tactics
de
por adulto (o preço varia de acordo com o tamanho do grupo)







