Potential Backdoor or FE Bypass - Scripting Support - Developer
Por um escritor misterioso
Descrição

MERCURY and DEV-1084: Destructive attack on hybrid environme - vulnerability database

What is System Hacking in Ethical Hacking? How to Prevent from It

Most exploited critical vulnerabilities and zero days trend in 2022 - CYFIRMA

Hackers Actively Searching for Unpatched Microsoft Exchange - vulnerability database

CISSP Combined Notes, PDF, Cryptography

Reverse, Reveal, Recover: Windows Defender Quarantine Forensics, NCC Group Research Blog
Hack the Box - Crossfit Writeup
Updated MATA attacks industrial companies in Eastern Europe

Cyber resilience and cyber security issues of intelligent cloud computing systems - ScienceDirect
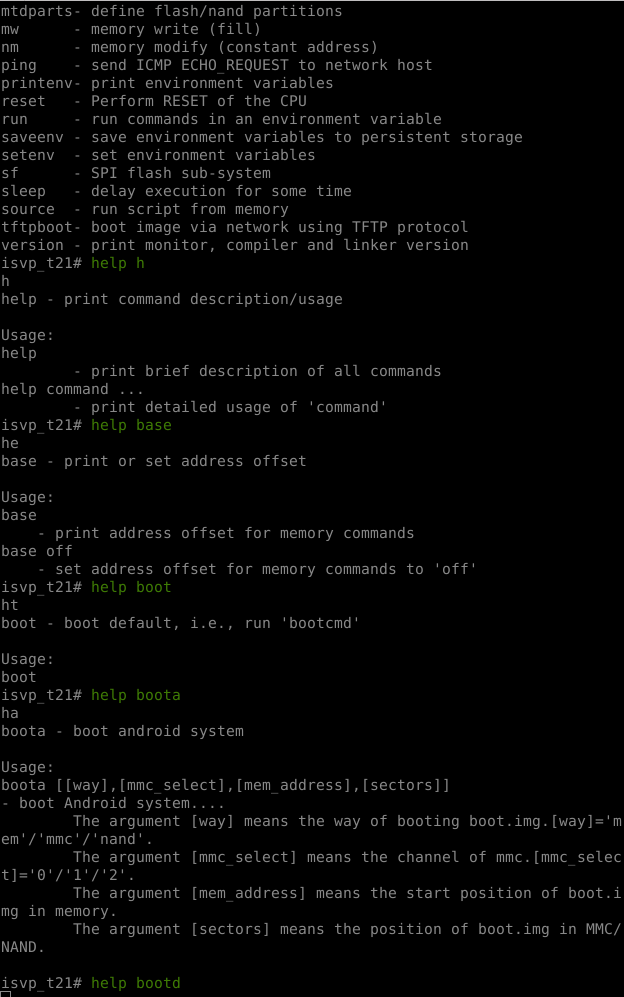
I hack, U-Boot
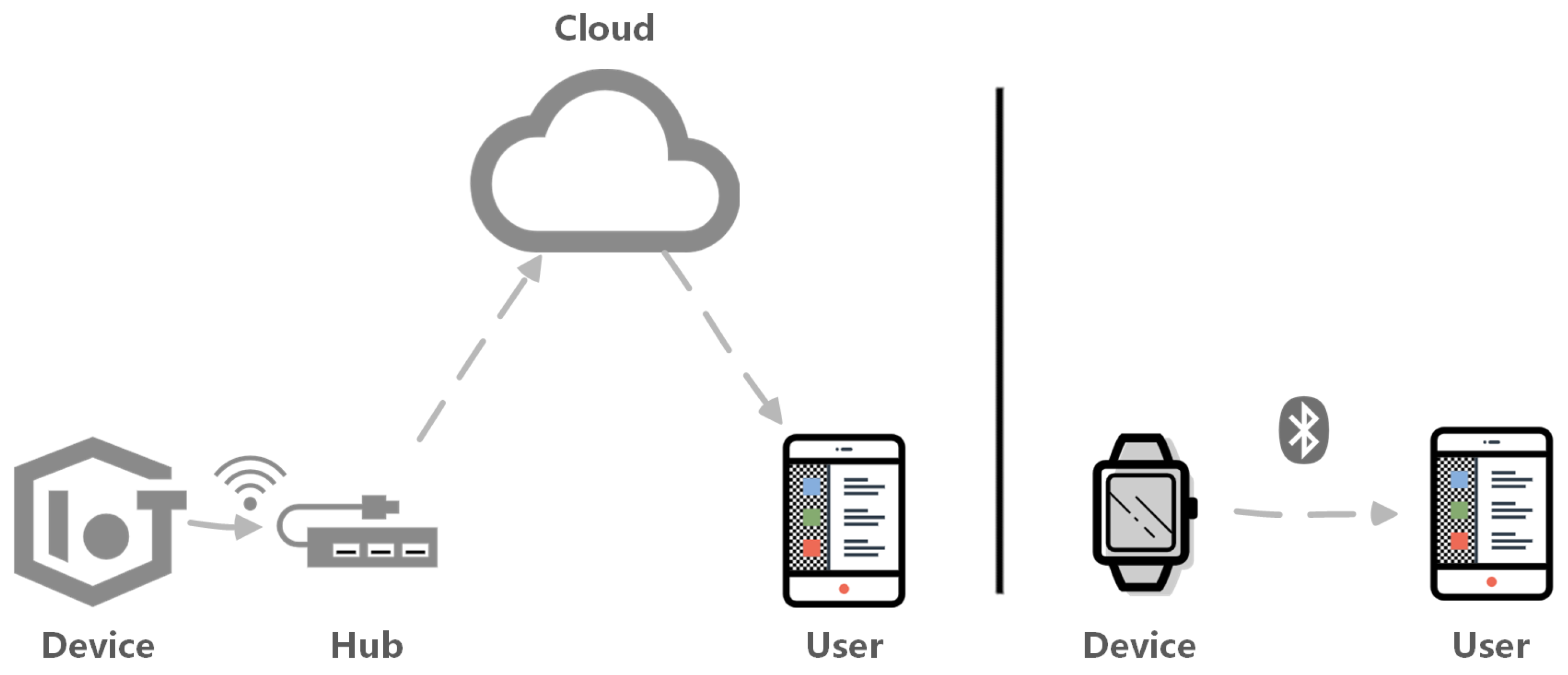
Future Internet, Free Full-Text

OWASP Testing Guide v3
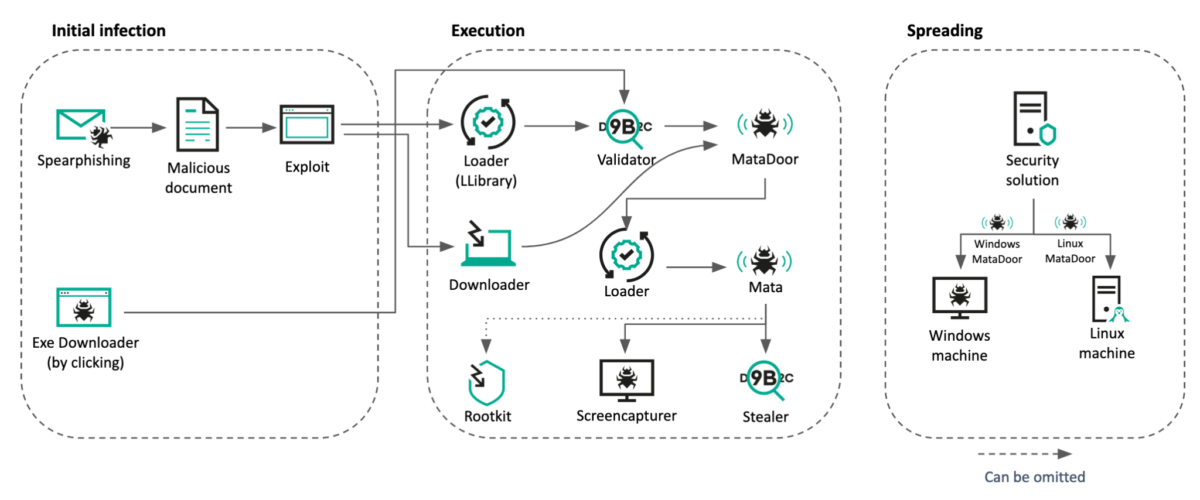
Updated MATA attacks industrial companies in Eastern Europe

THE CHANGING CYBER THREAT LANDSCAPE: ASIA-PACIFIC (APAC) REGION - CYFIRMA
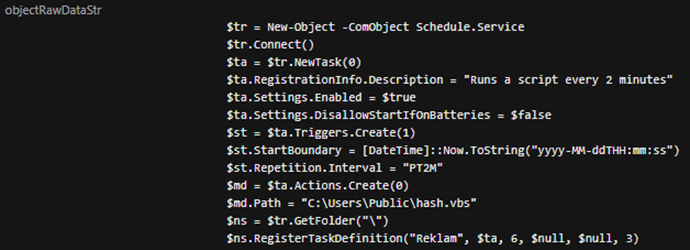
Analyzing AsyncRAT's Code Injection into Aspnet_Compiler.exe Across Multiple Incident Response Cases
de
por adulto (o preço varia de acordo com o tamanho do grupo)







