Malware analysis
Por um escritor misterioso
Descrição
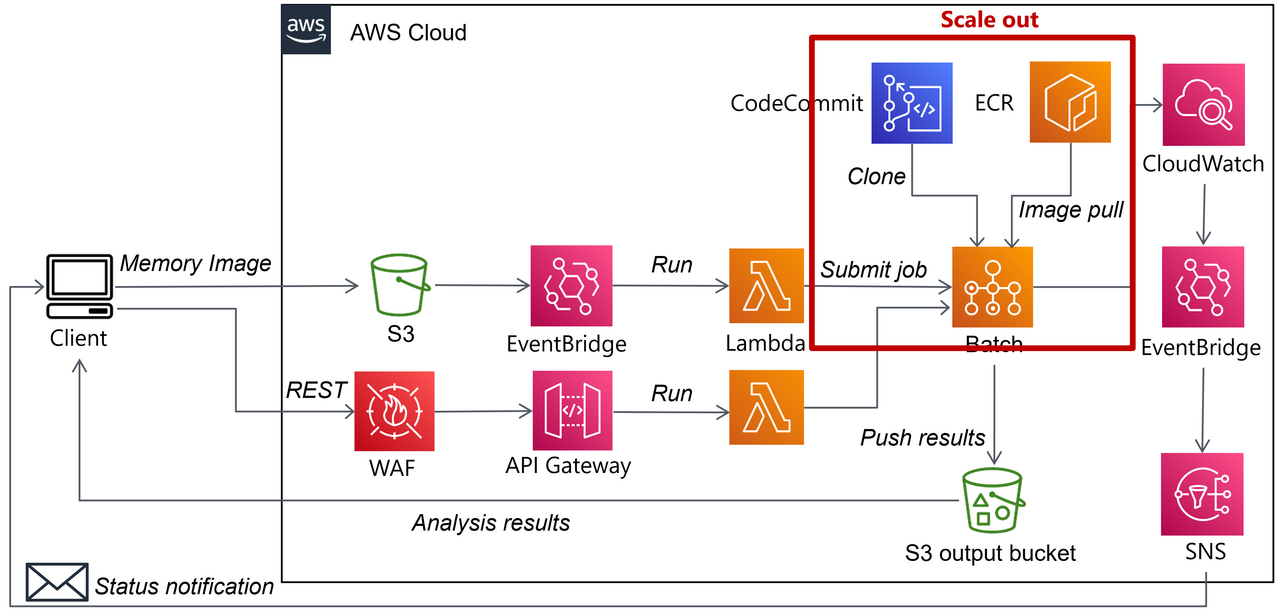
Automating Malware Analysis Operations (MAOps) - JPCERT/CC Eyes

Is Malware Analysis Right for Your Business?
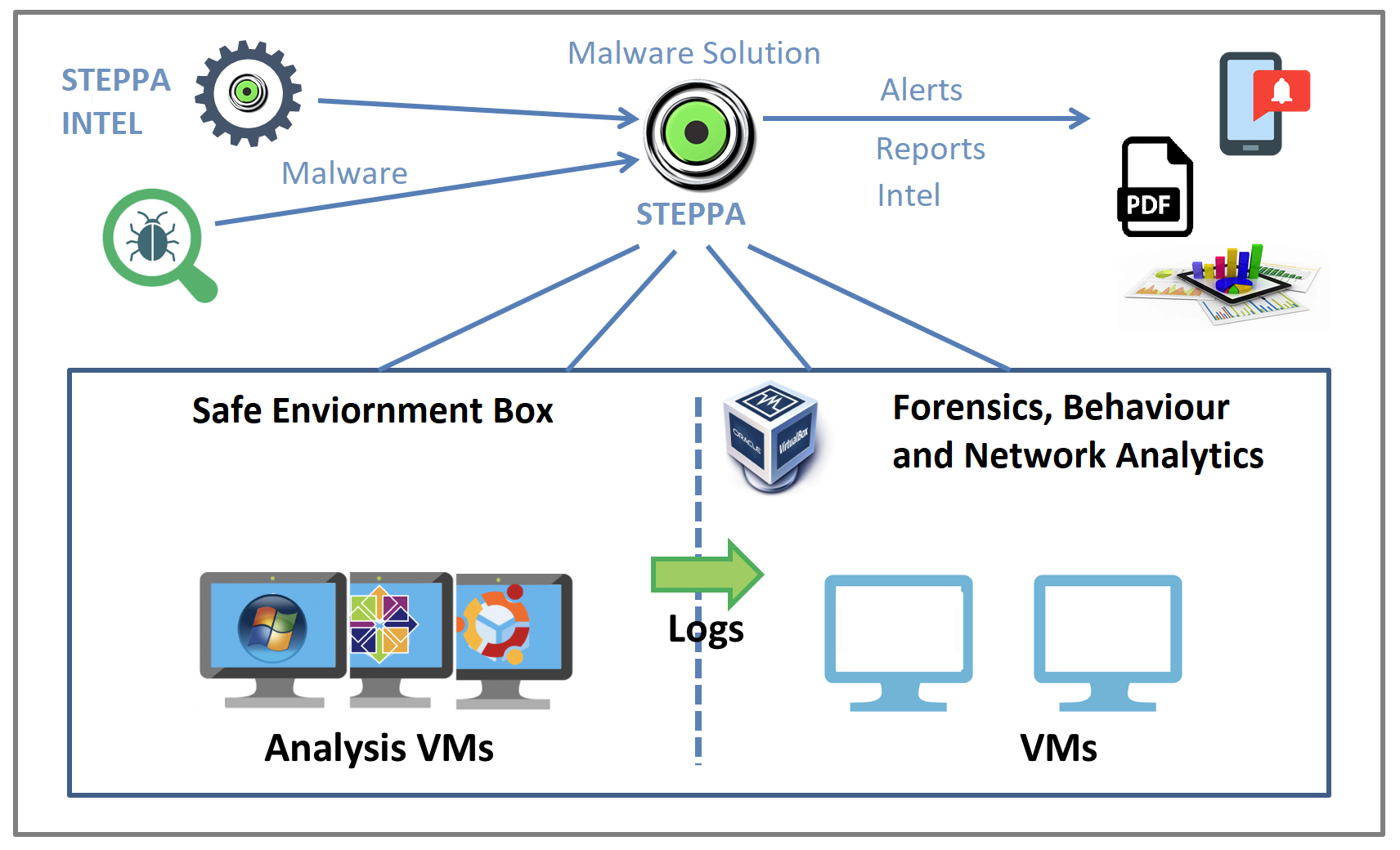
Malware Analysis Solution: Analyze, Detect, and Protect
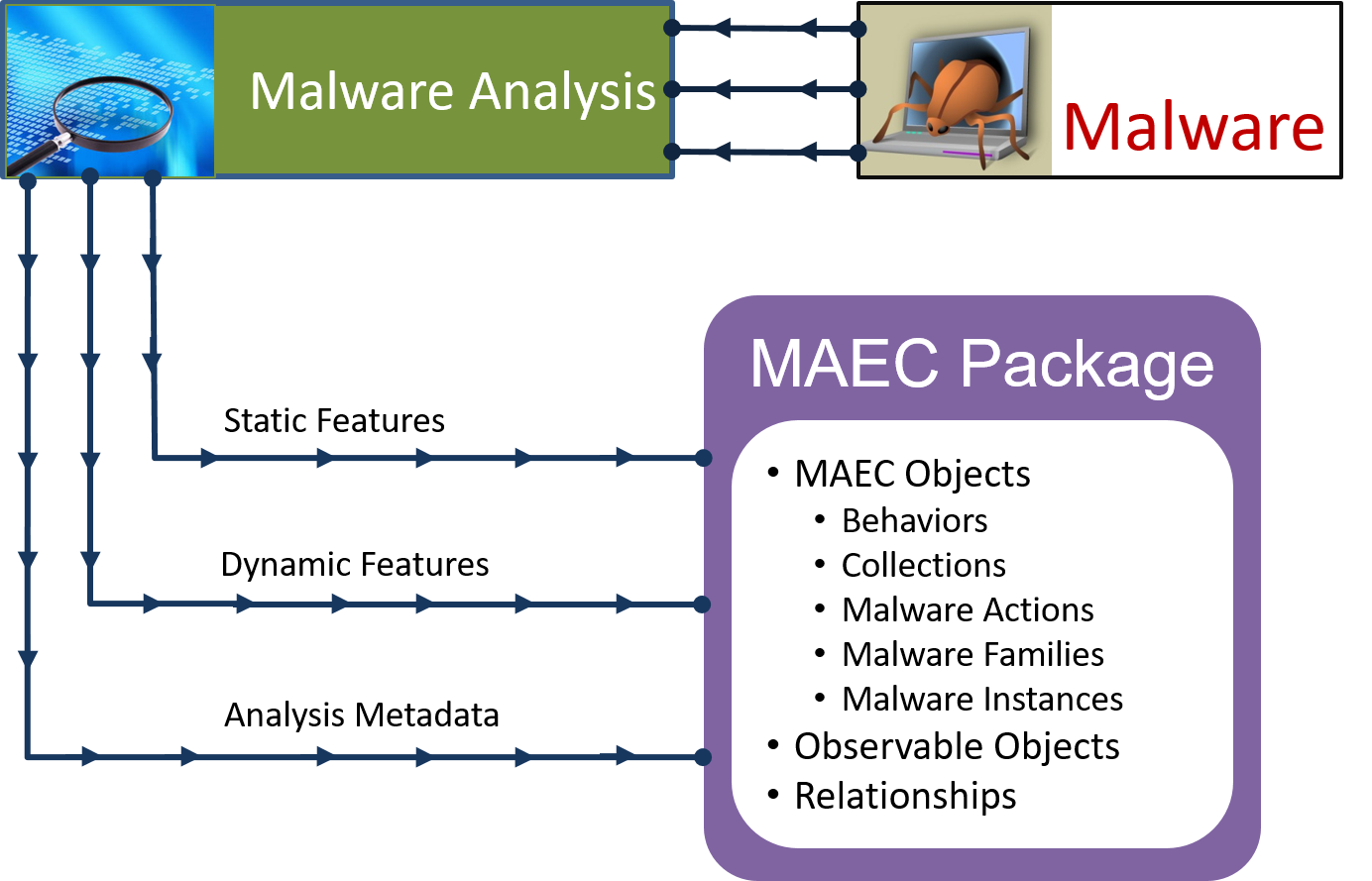
Static and Dynamic Malware Analysis

Malware Analysis: Tips, Tools, and Techniques

Figure .: Pros and Cons of Malware Analysis Methods
Introduction to Malware Analysis Course

5 Steps for Secure Malware Analysis
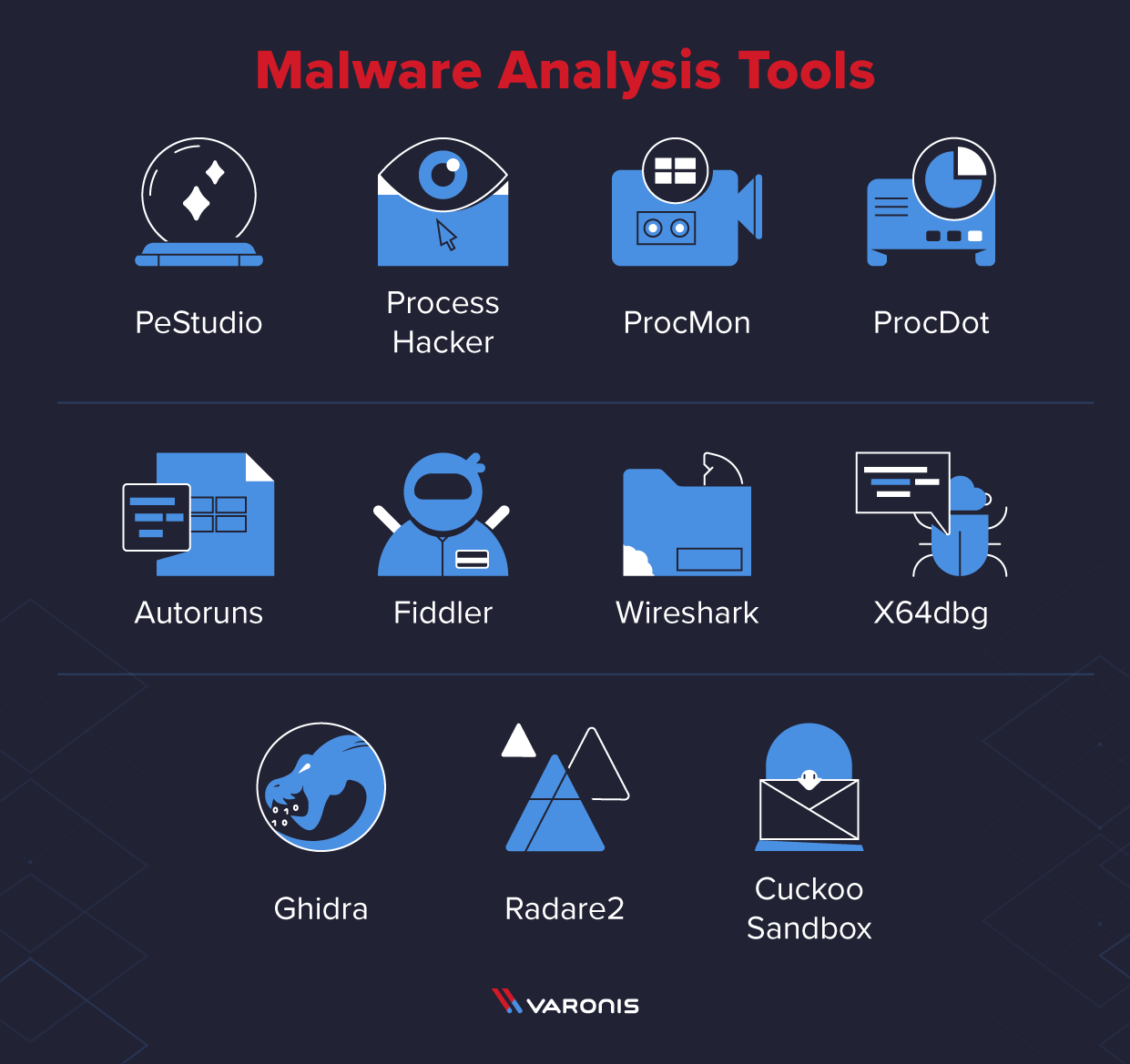
11 Best Malware Analysis Tools and Their Features

A Guide for Beginners in Malware Analysis: The Roadmap, Job Career, Pay, Future and more..
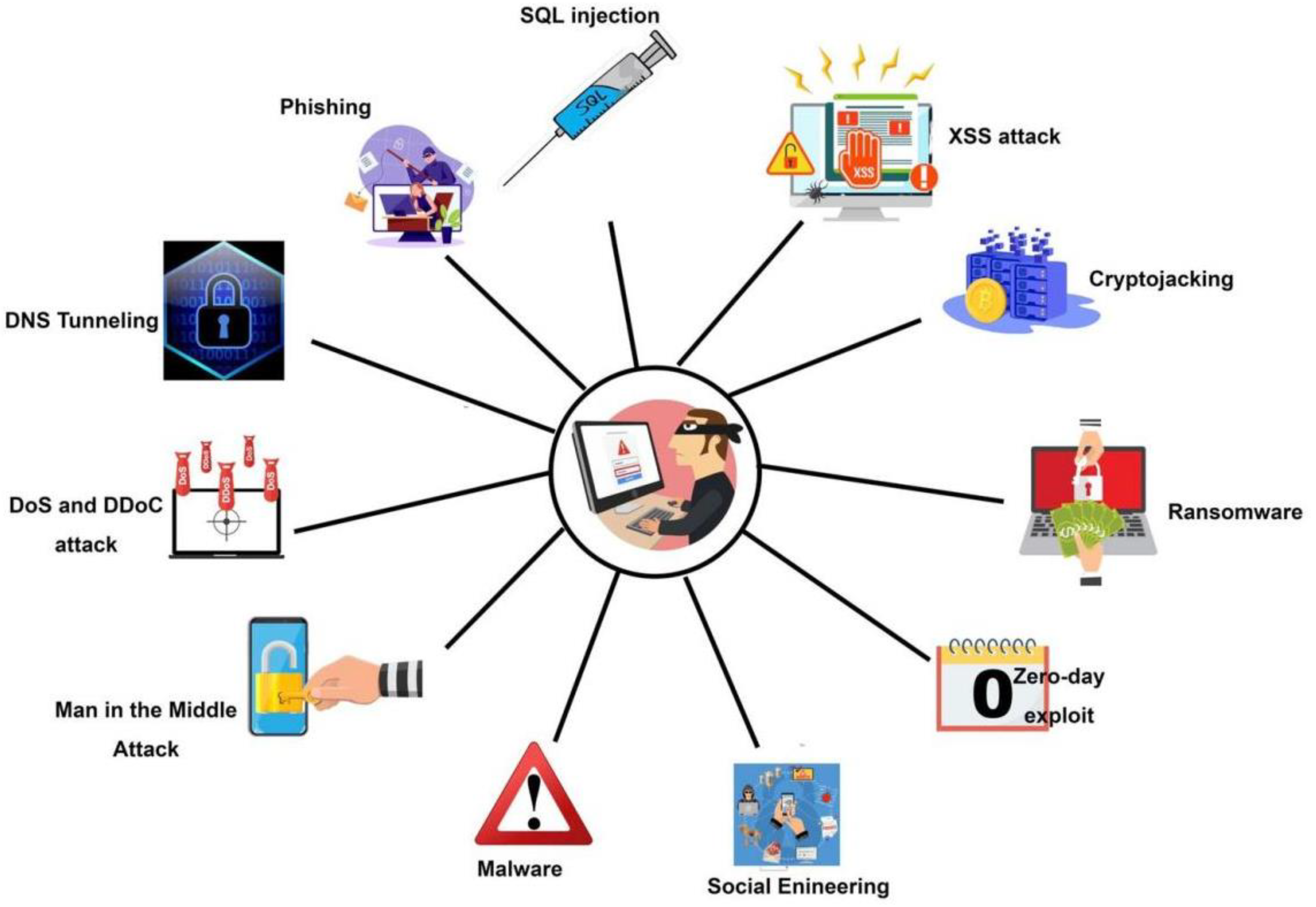
Symmetry, Free Full-Text
de
por adulto (o preço varia de acordo com o tamanho do grupo)







