Malware analysis
Por um escritor misterioso
Descrição

Malware Analysis - Prestige Ransomware

The Top 20 Malware Analysis Tools for 2024
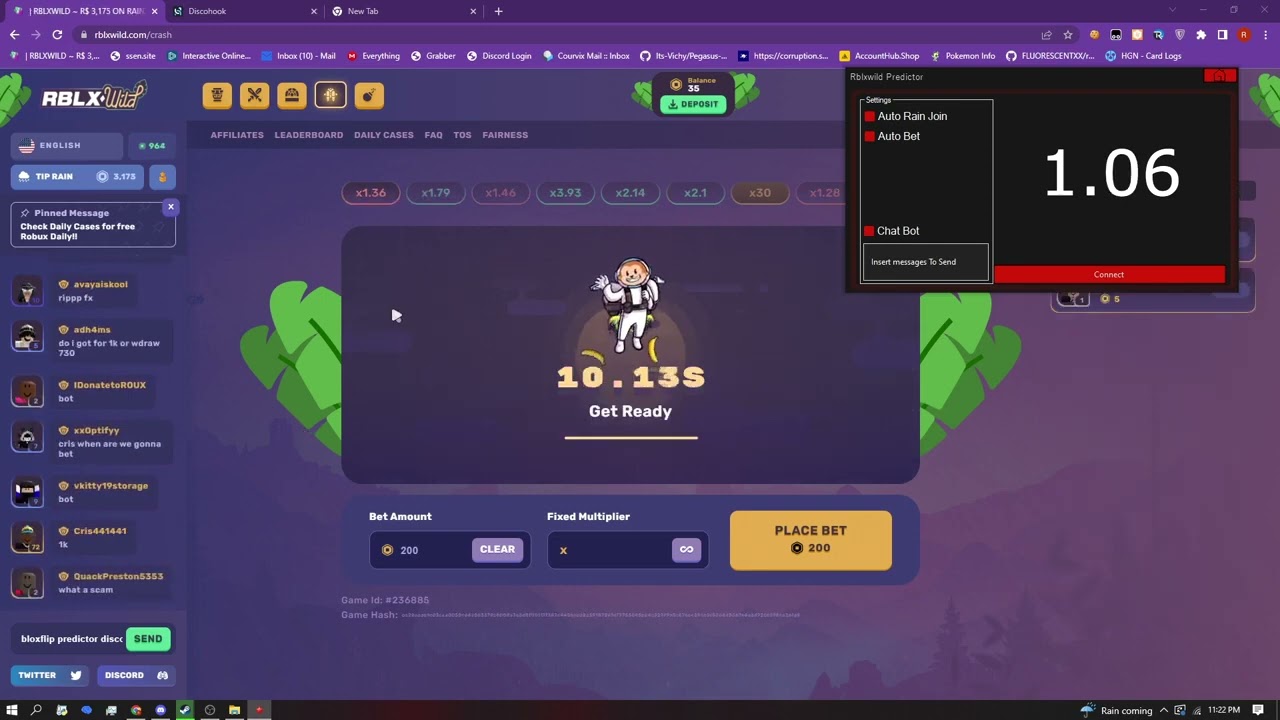
Mastering 4 Stages of Malware Analysis

Malware Analysis: Protecting Your Network from Cyber Attacks

Malware Analysis: Steps & Examples - CrowdStrike

What is Malware Analysis? Benefits, Types, and Tools

The Role of Malware Analysis in Cybersecurity

Malware Analysis Fundamentals
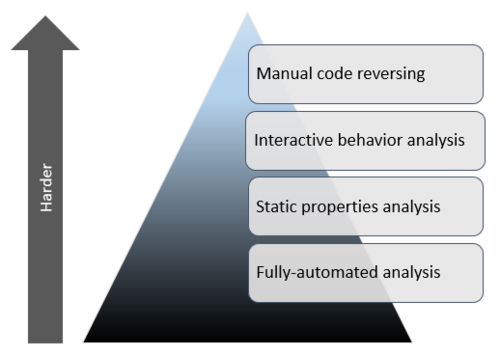
IIJ Malware Analysis Solution, Business
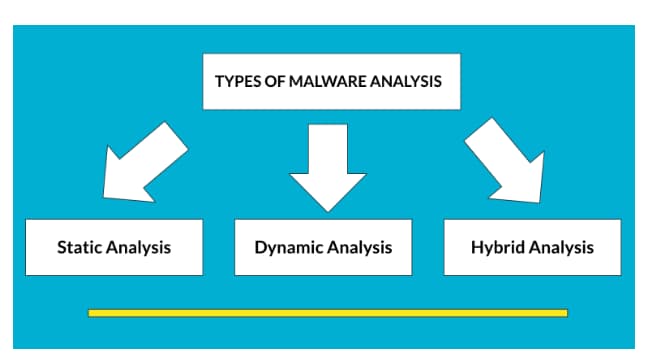
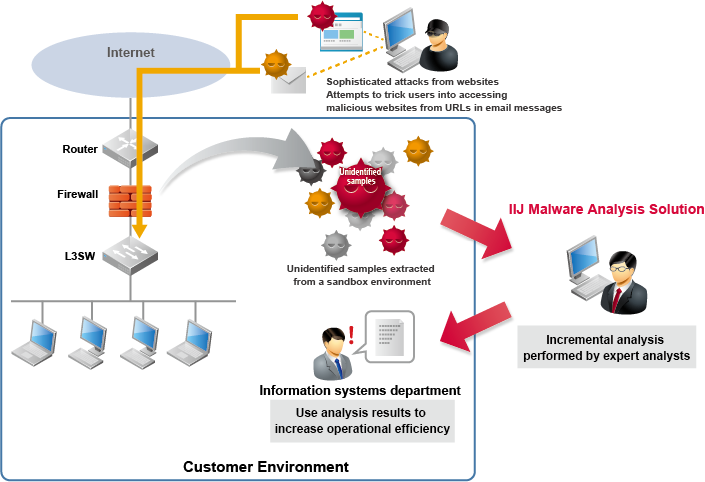
Malware Analysis: Techniques and Tools

Detail procedure of malware analysis
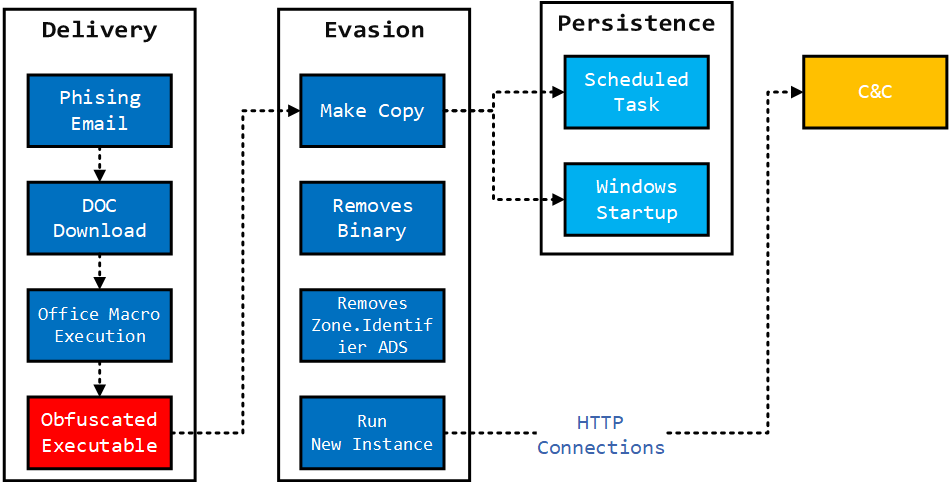
Advanced Windows Malware Analysis - Acquiring Memory Artifacts

Figure .: Pros and Cons of Malware Analysis Methods
de
por adulto (o preço varia de acordo com o tamanho do grupo)