Malware analysis
Por um escritor misterioso
Descrição
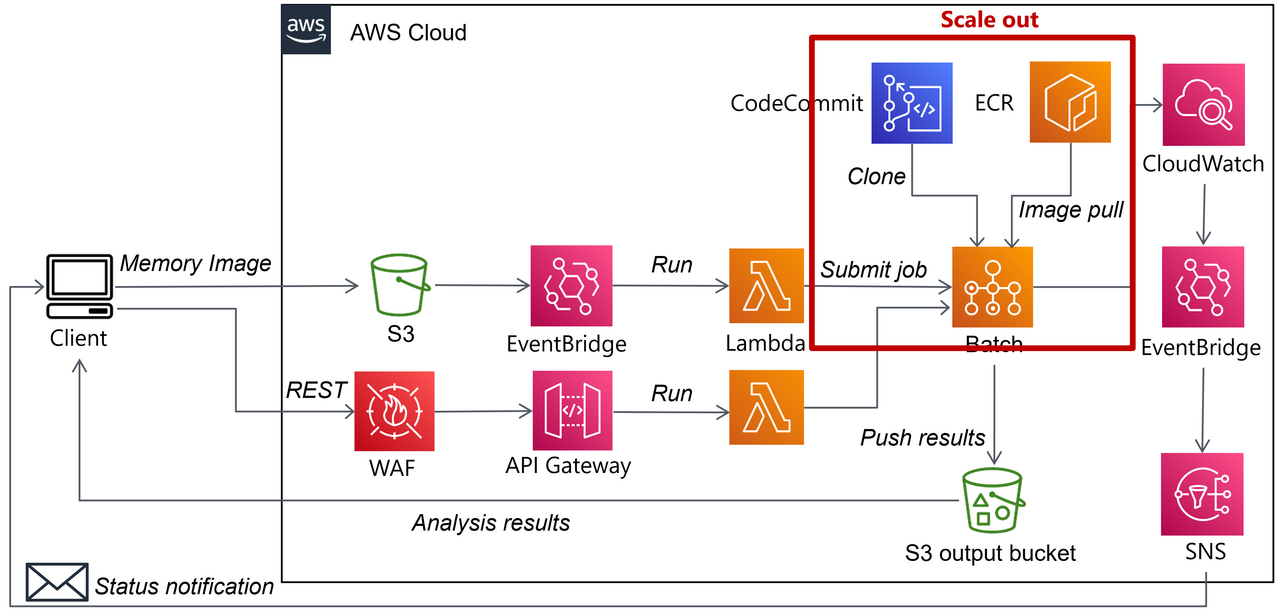
Automating Malware Analysis Operations (MAOps) - JPCERT/CC Eyes

How to Become a Malware Analyst [+ Career & Salary Guide]
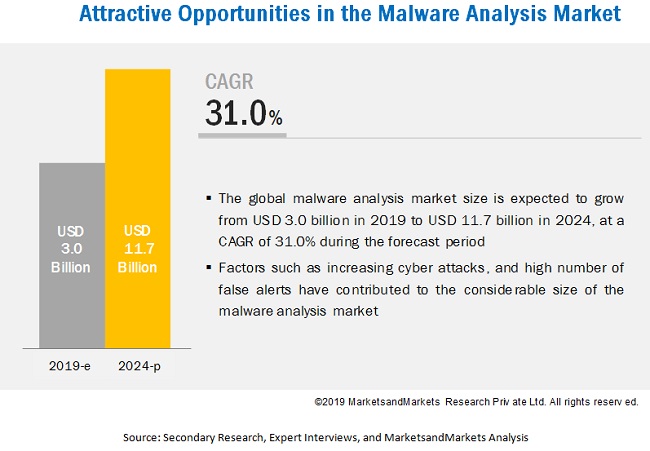
Malware Analysis Market Growth Drivers & Opportunities

What Is Malware Analysis? Definition, Types, Stages, and Best Practices - Spiceworks

Learn to Analyze Malware - (The Malware Analysis Project 101)
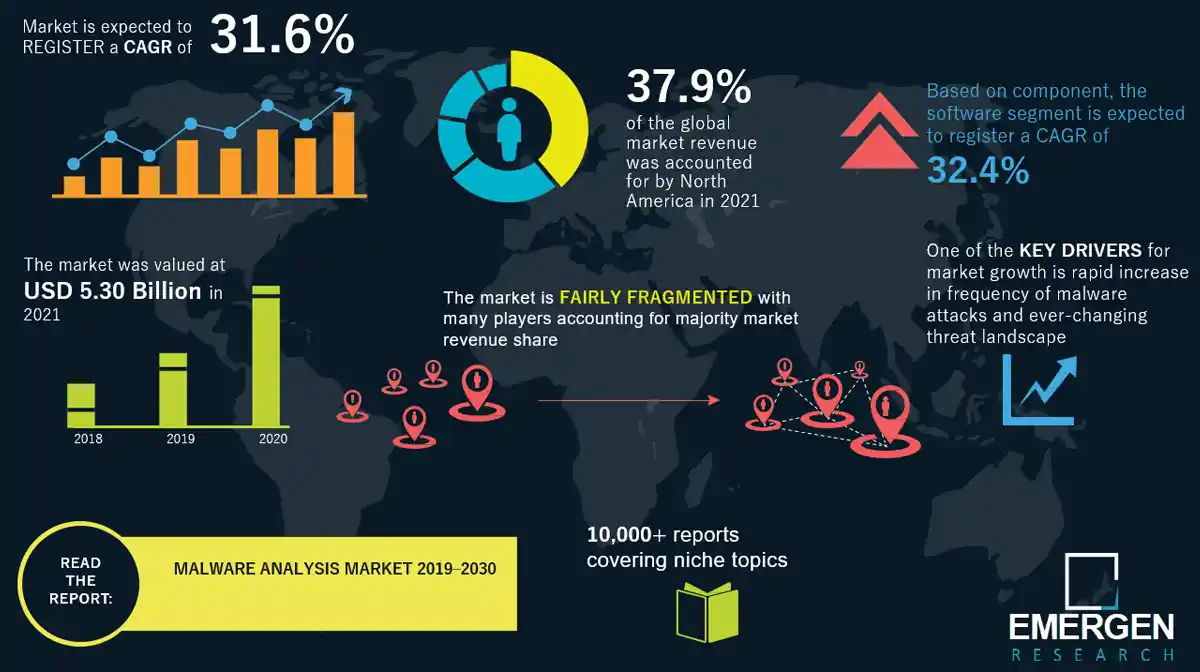
Malware Analysis Market Trend
Master Reverse Engineering, Malware Analysis, Linux, Cyber Security, Ghidra,x86-64, IDA Pro, IDA Free, Assembly and NASM

Mastering Reverse Engineering & Malware Analysis | REMASM+

The Top 10 Malware Analysis Tools
What is Malware Analysis? - SOC Prime
Malware Analysis: A General Approach - Security Risk Advisors

CYBER 5W

What is Malware Analysis? Types and Stages of Malware Analysis

Malware Analysis - Credly
Highlight, take notes, and search in the book In this edition, page numbers are just like the physical edition

Malware Analysis and Detection Engineering: A Comprehensive Approach to Detect and Analyze Modern Malware
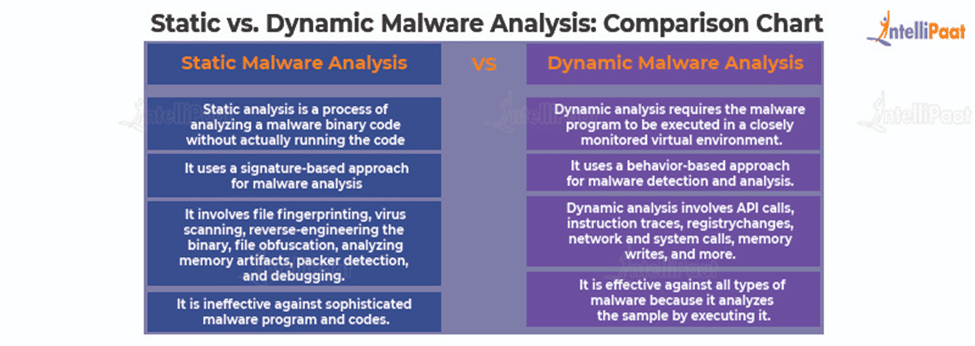
Malware Analysis - What is, Benefits & Types (Easily Explained)
de
por adulto (o preço varia de acordo com o tamanho do grupo)