Malware analysis Malicious activity
Por um escritor misterioso
Descrição

Endpoint Detection and Response, Free - What is EDR Security?

PROUD-MAL: static analysis-based progressive framework for deep unsupervised malware classification of windows portable executable
Malware analysis Malicious activity
Malware analysis AIO_4.9.8__ed.rar Malicious activity
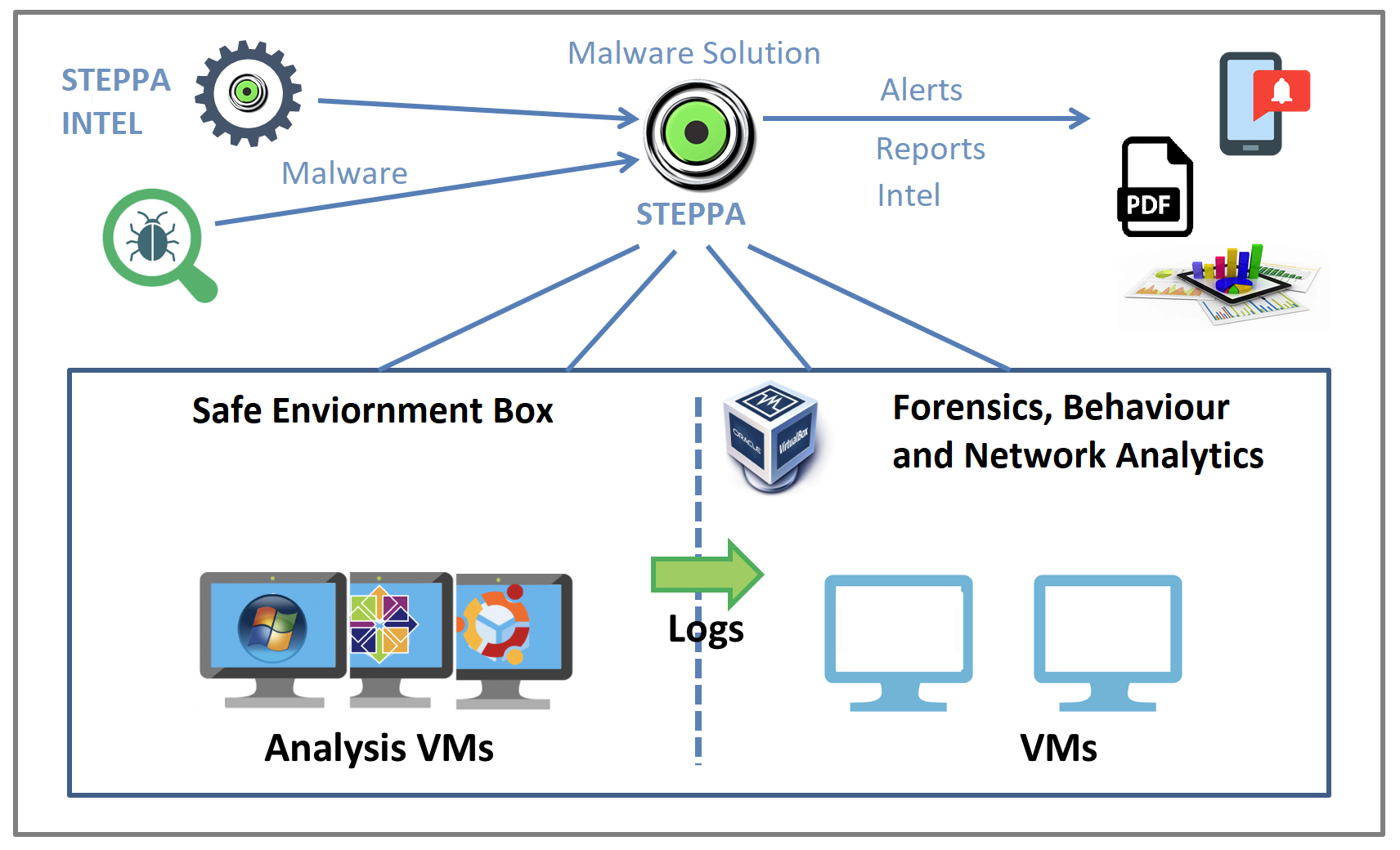
Malware Analysis Solution: Analyze, Detect, and Protect

PROUD-MAL: static analysis-based progressive framework for deep unsupervised malware classification of windows portable executable
Malware analysis 1071d6d497a10cef44db396c07ccde65 Malicious activity

Malware analysis mykey_.rar Malicious activity

Cybersecurity Search Engine

Patch Now: Exploit Activity Mounts for Dangerous Apache Struts 2 Bug

Malware Analysis: Steps & Examples - CrowdStrike

Robust Malware Detection Models: Learning From Adversarial Attacks and Defenses - Forensic Focus
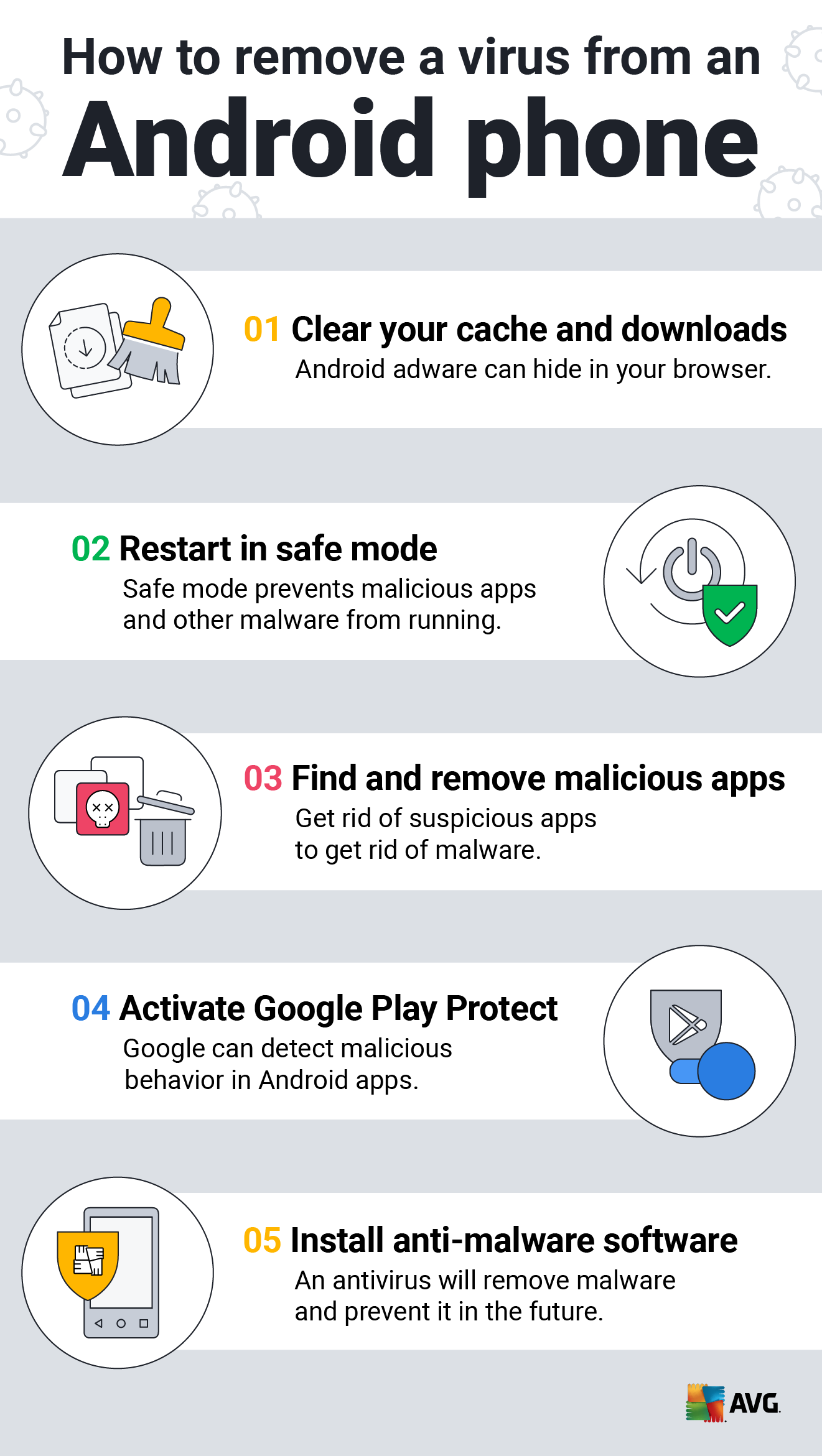
How to Clean an Android or iPhone from Viruses for Free

What is Malware? Definition, Types, Prevention - TechTarget
de
por adulto (o preço varia de acordo com o tamanho do grupo)







