Malware analysis Malicious activity
Por um escritor misterioso
Descrição

Mastering Malware Analysis

Malware Analysis: Steps & Examples - CrowdStrike

Cybersecurity News, Insights and Analysis
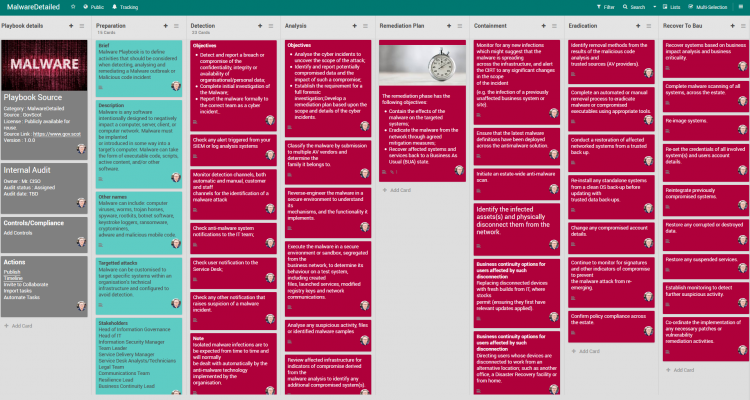
Playbook for Malware outbreak

What is Malware? Definition, Types, Prevention - TechTarget
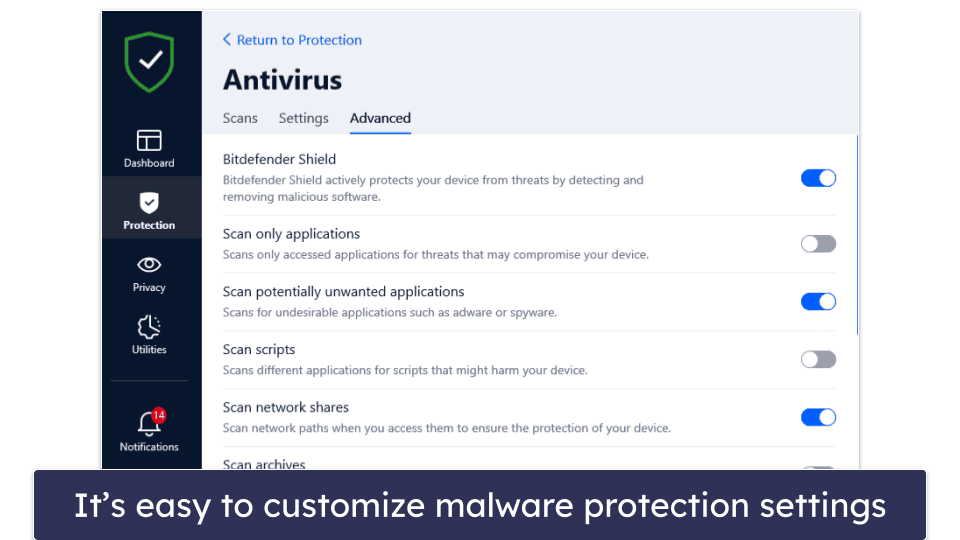
10 Best Antivirus Software in 2023: Windows, Android, iOS, Mac
Malware analysis AIO_4.9.8__ed.rar Malicious activity

Malware Analysis: Steps & Examples - CrowdStrike

Robust Malware Detection Models: Learning From Adversarial Attacks and Defenses - Forensic Focus
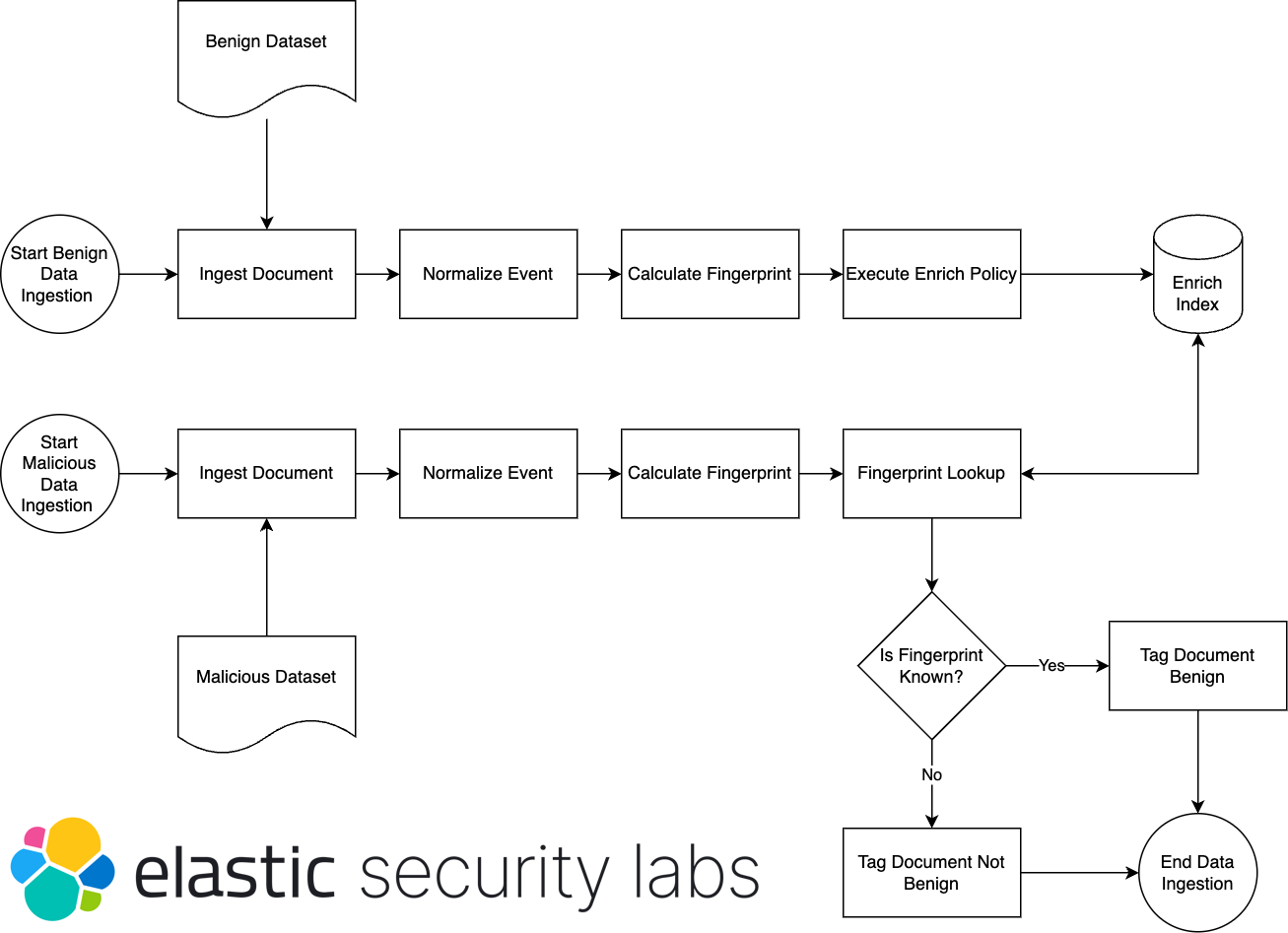
An Elastic approach to large-scale dynamic malware analysis — Elastic Security Labs
de
por adulto (o preço varia de acordo com o tamanho do grupo)