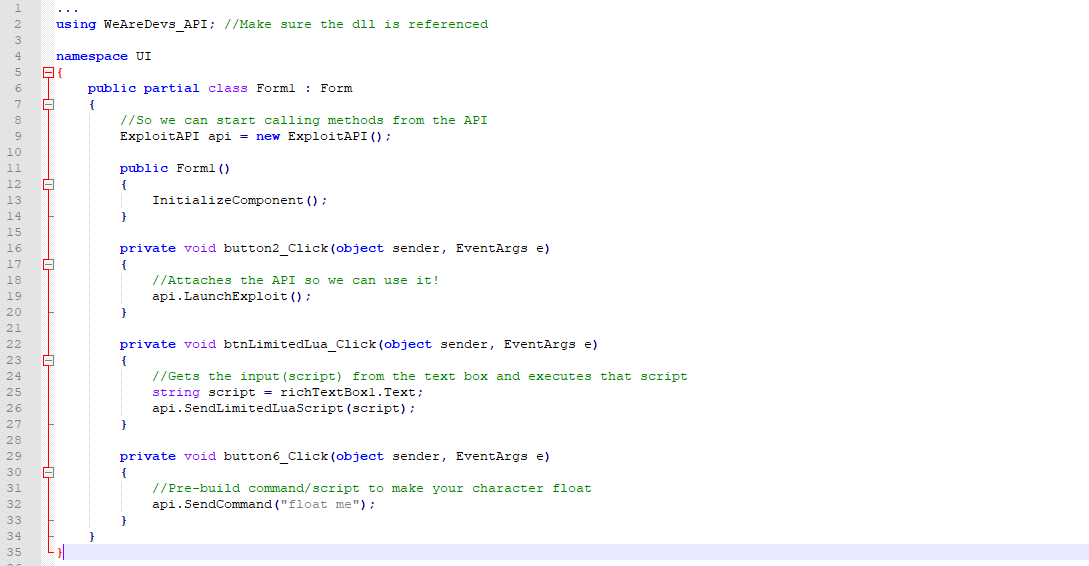
Malware analysis Malicious activity
Por um escritor misterioso
Descrição
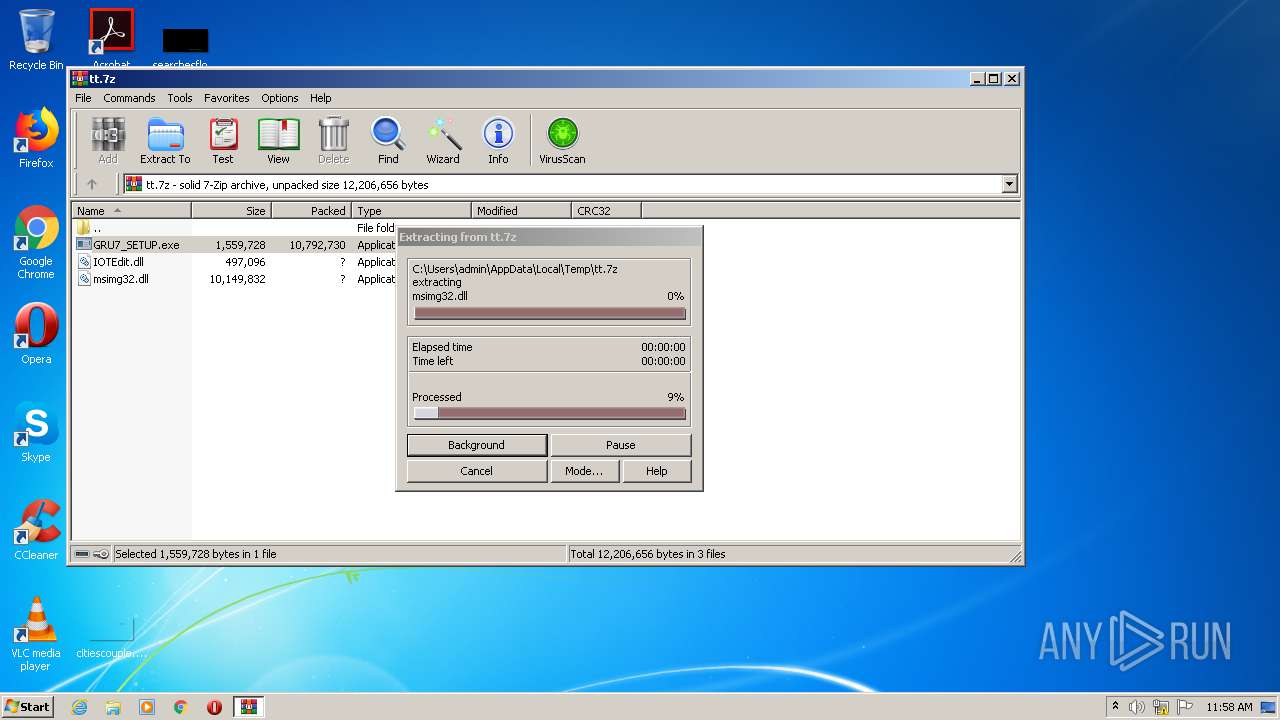
Malware analysis tt.7z Malicious activity

Security Orchestration Use Case: Automating Malware Analysis - Palo Alto Networks Blog
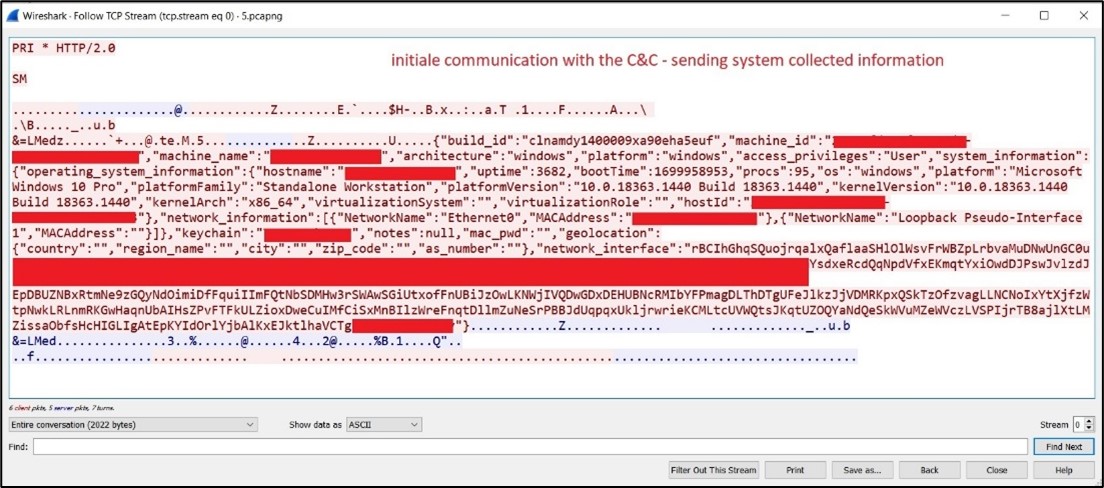
Behind the Scenes: JaskaGO's Coordinated Strike on macOS and Windows

Malware analysis mykey_.rar Malicious activity

Malware Analysis: Protecting Your Network from Cyber Attacks

Cybersecurity Search Engine

AlienVault - Open Threat Exchange

Routers Roasting on an Open Firewall: the KV-botnet Investigation - Lumen

Building A Simple Malware Analysis Pipeline In The Homelab Pt - 1 · Arch Cloud Labs

Endpoint Detection and Response, Free - What is EDR Security?

Detail procedure of malware analysis
de
por adulto (o preço varia de acordo com o tamanho do grupo)