Indirect Command Execution – Penetration Testing Lab
Por um escritor misterioso
Descrição
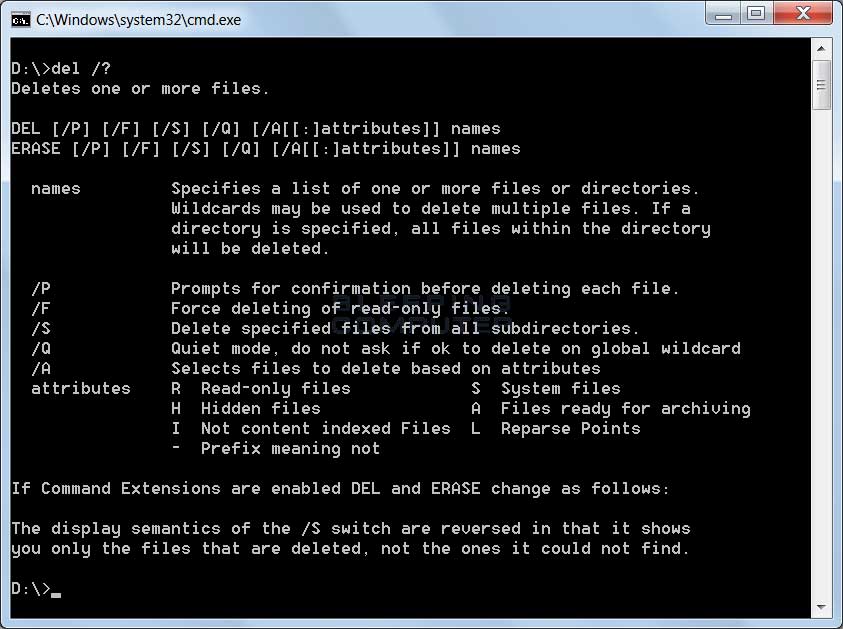
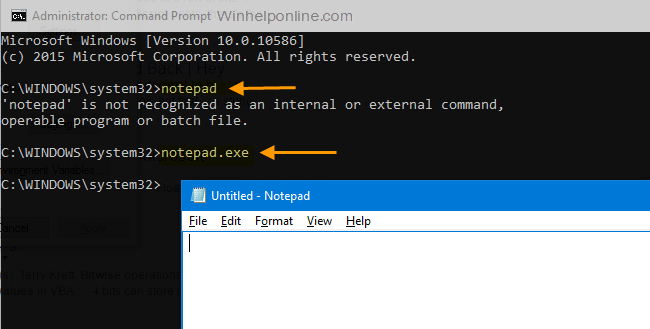
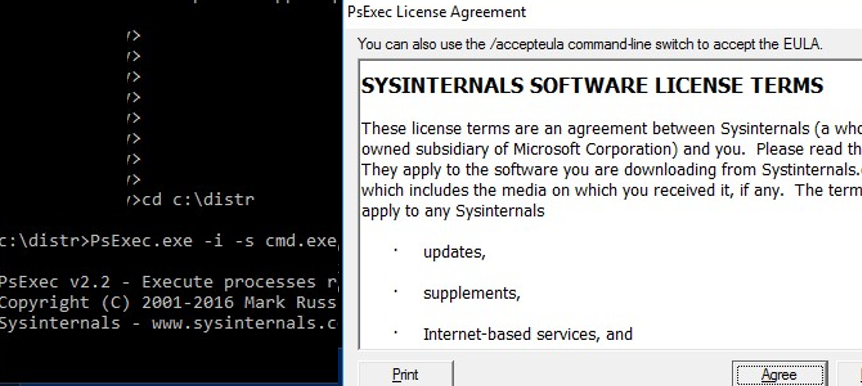
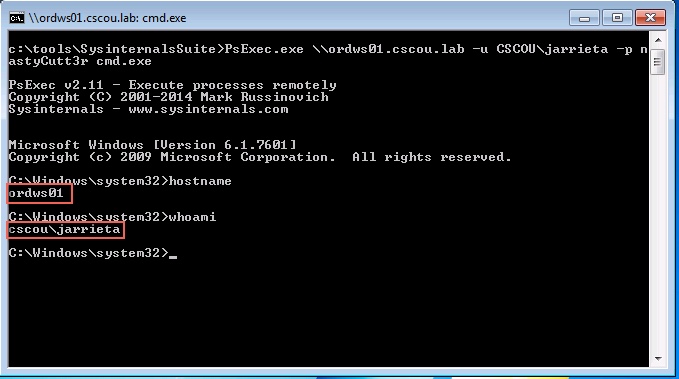
The windows ecosystem provides multiple binaries that could be used by adversaries to execute arbitrary commands that will evade detection especially in environments that are monitoring binaries such as "cmd.exe". In certain occasions the techniques described below could be used to bypass application whitelisting products if rules are not configured properly (whitelist by path or…

How to Prevent SQL Injection Attacks?
Kali Linux Penetration Testing Tutorial: How to Use Kali Linux
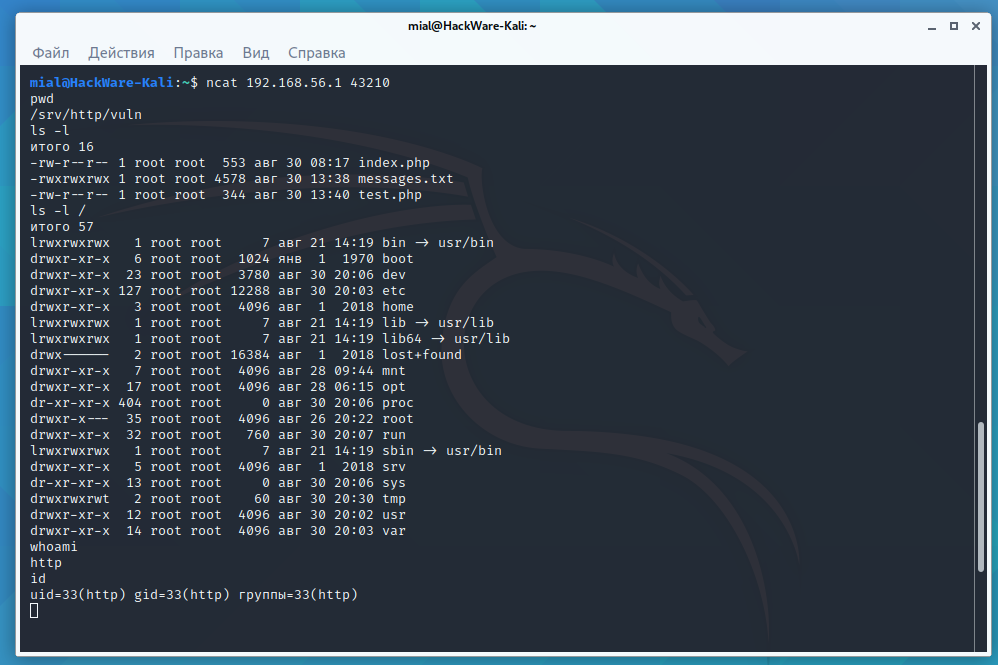
How to exploit blind command injection vulnerability - Ethical hacking and penetration testing

Indirect Command Execution – Penetration Testing Lab

Denial-of-service attack - Wikipedia
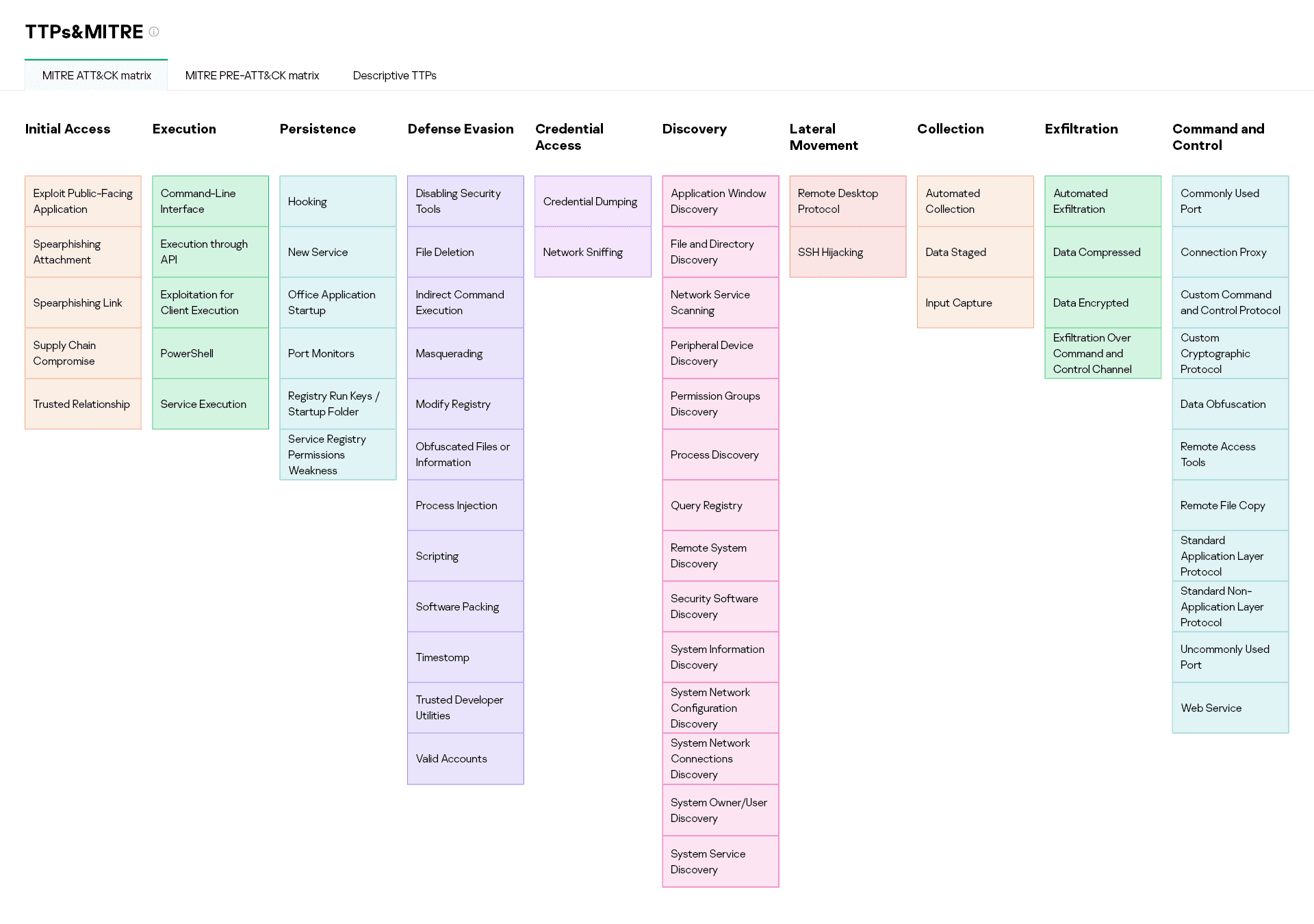
ATT&CK in APT Reports

Cyber Operations during the Russo-Ukrainian War

Low cost 3D printing of metals using filled polymer pellets - ScienceDirect

Command Injection - Lab #3 Blind OS command injection with output redirection
Penetration Testing Lab 15 by Pentestit — walkthrough
de
por adulto (o preço varia de acordo com o tamanho do grupo)