The Unacceptable Flaw with : Use of Game Explorer/DB in
Por um escritor misterioso
Descrição
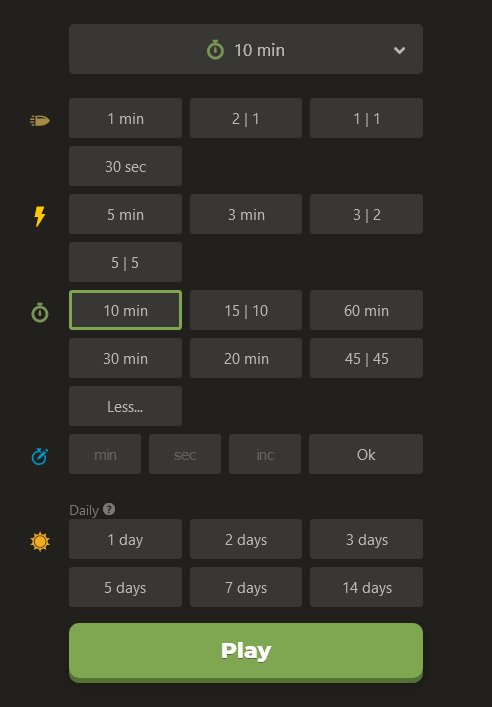
DO YOU REALIZE THAT YOUR TURN BASED OPPONENT CAN LEGALLY PLAY THE WORLD'S BEST CHESS MOVE AGAINST YOU FOR THE ENTIRE OPENING? That as long as you stay in book (which means making a good move), they can choose the most preferred move from the collection of Masters and Grandmasters since the 1800s against
Sorry if this is a silly Question Please be gentle, I'm new
:max_bytes(150000):strip_icc()/51-attack.asp-final-b97e967390ea40028ff9ddf30d2ee6c5.png)
51% Attack: Definition, Who Is At Risk, Example, and Cost
You've been detected…, Your ship is exposed…, An alarm blares…, “Torpedo incoming!”, Objec

Objects in Space

Building Interactive Enterprise Grade Applications with Open AI

FPGAs: Security Through Obscurity?

ACT! By Sage 2008 10.0 [OLD VERSION] : Electronics

What is Peer to Peer Network, and How does it work? [UPDATED
I developed an algorithm capable of finding all the areas that a
Dual-Process Theory - FourWeekMBA

Dell XPS 27 review: A high-end PC with 4K display and awesome

A Log4J Vulnerability Has Set the Internet 'On Fire

Microsoft Ignite 2023 Book of News

Hackers Using Microsoft MSHTML Flaw to Spy on Targeted PCs w
de
por adulto (o preço varia de acordo com o tamanho do grupo)