Visão geral do Identity-Aware Proxy
Por um escritor misterioso
Descrição
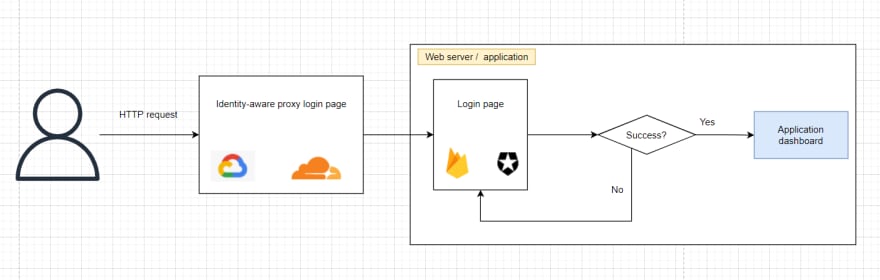
🔐 Authentication: Is Identity-aware Proxy enough for most use cases? - DEV Community
Spring Cloud GCP IAP Authentication and Authorization - Knoldus Blogs
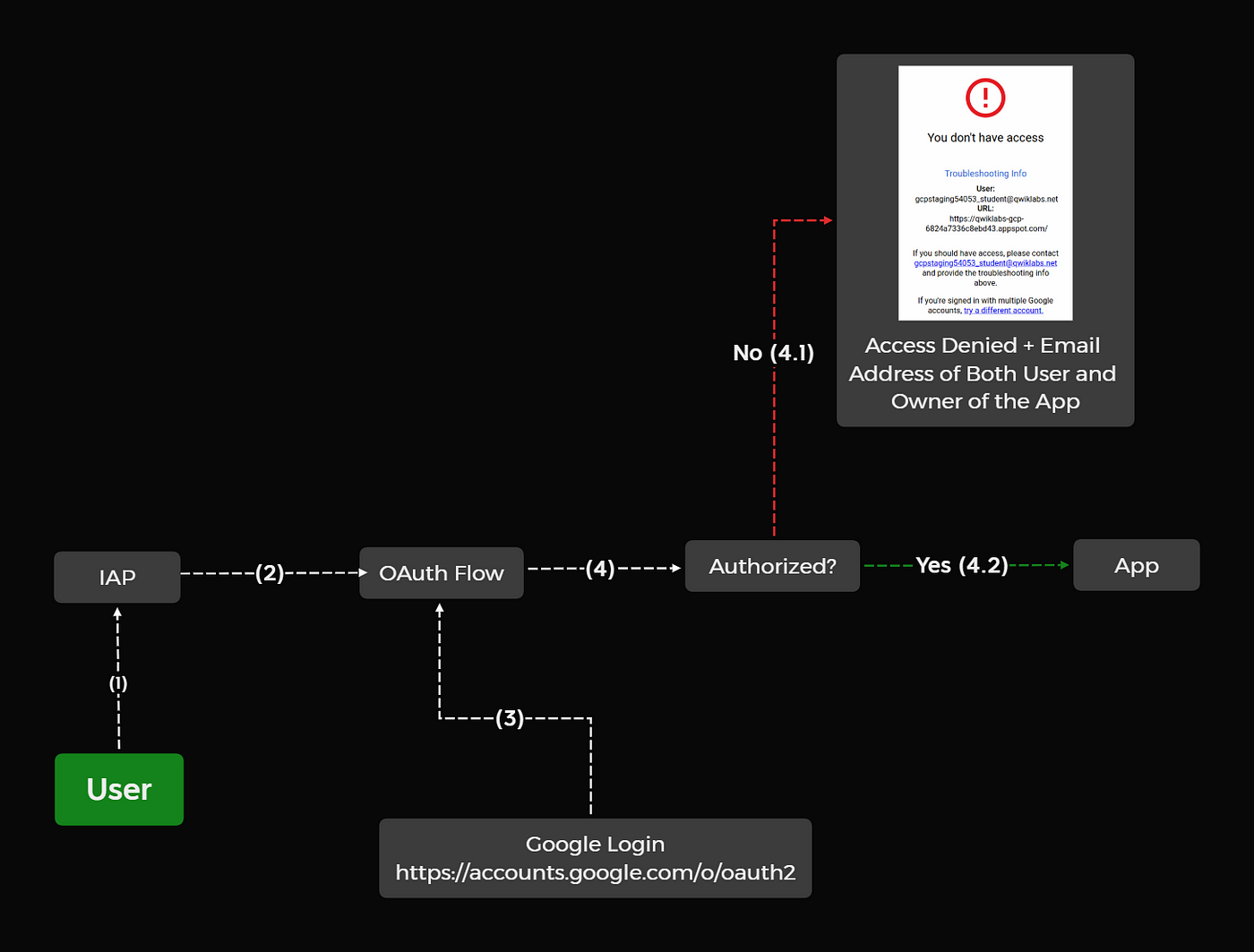
Identity-Aware Proxy Misconfiguration- Google Cloud Vulnerability, by Borna Nematzadeh
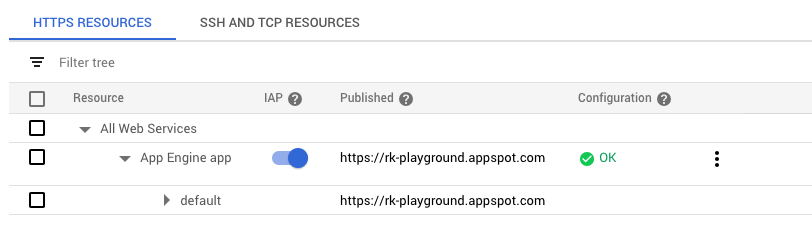
API Authentication with GCP Identity-Aware Proxy, by Tyler Treat
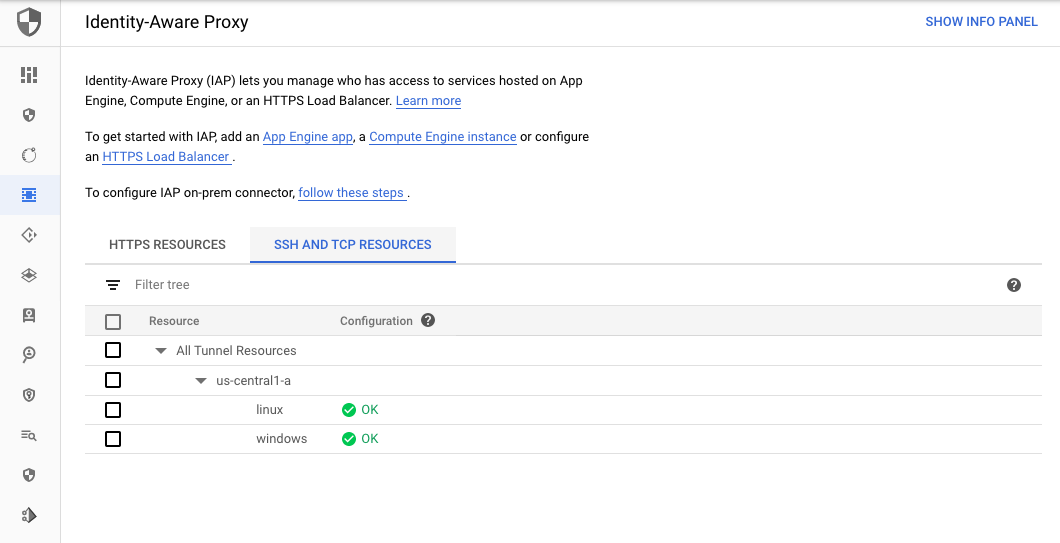
Securing Remote Access with Google Cloud Identity-Aware Proxy (IAP) – Woolpert
Google Cloud Tech on X: Manage access to applications easily and securely with Cloud Identity-Aware Proxy / X

Overview of IAP for on-premises apps, Identity-Aware Proxy

Sysadmin Stories: Veeam Backup for Google Cloud - Zero Trust Architecture with Cloud Identity-Aware Proxy
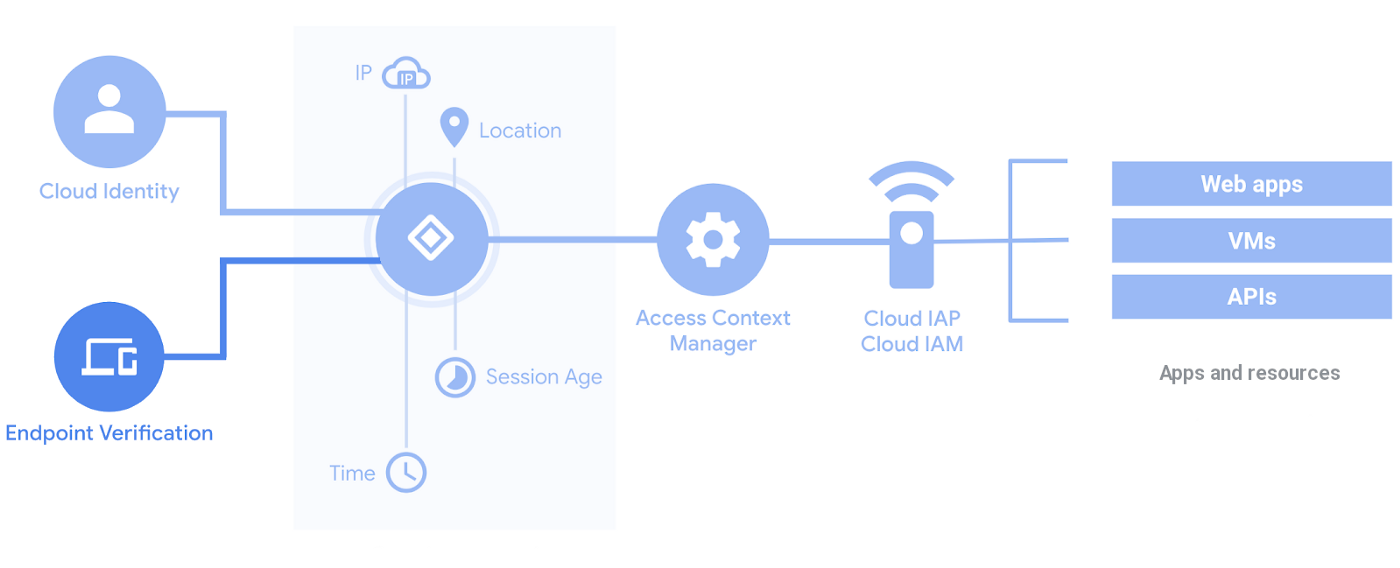
Kubernetic - Blog

GCP: Como usar Identity Aware Proxy no GCP
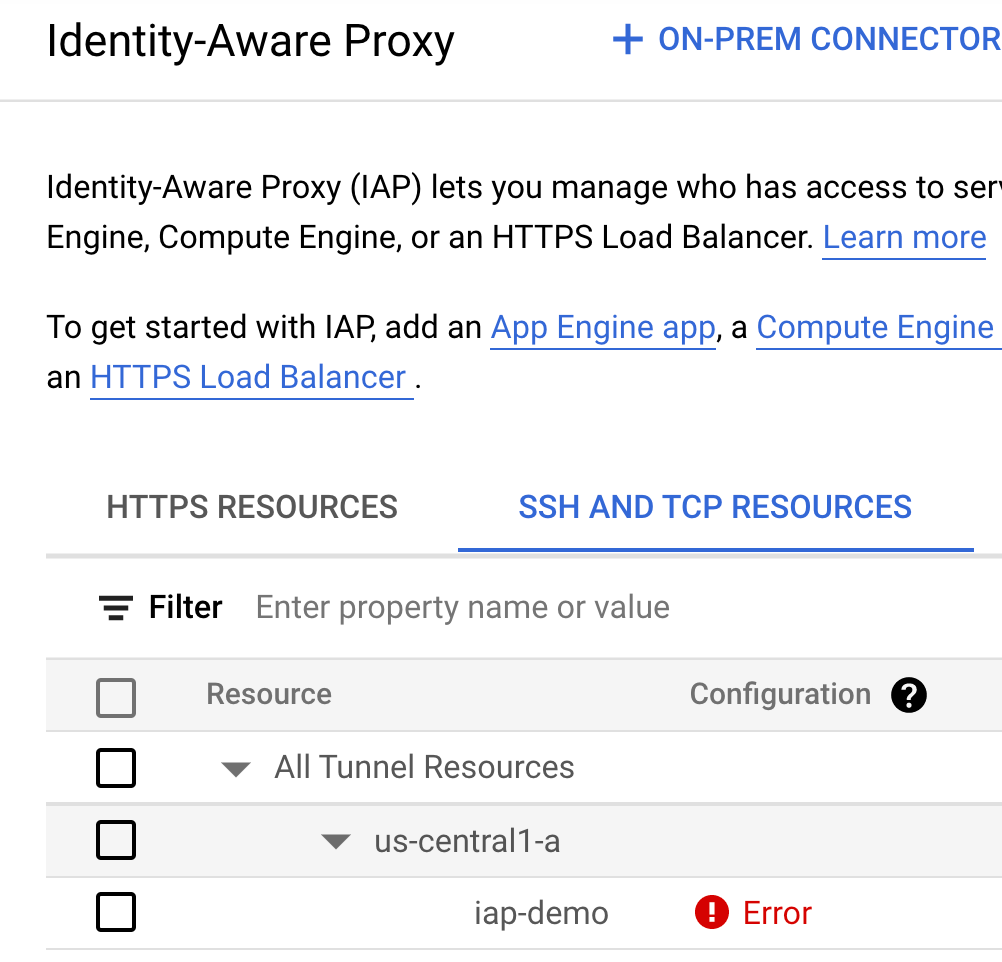
Utilizing GCP's Identity Aware Proxy to SSH into Internal-IP only VM's, by Jacob Luna
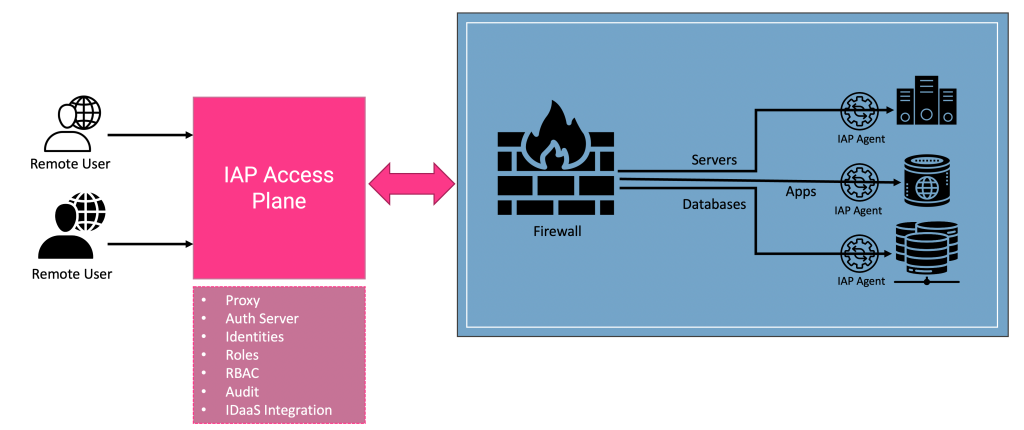
Zero Trust Network Security with Identity-Aware Proxies - The New Stack

Akamai Technologies - An identity-aware proxy is a broker that performs adaptive access controls using digital identities. Click here to find out the next step in your Zero Trust journey
de
por adulto (o preço varia de acordo com o tamanho do grupo)





