AiTM/ MFA phishing attacks in combination with new Microsoft protections (2023 edition)
Por um escritor misterioso
Descrição
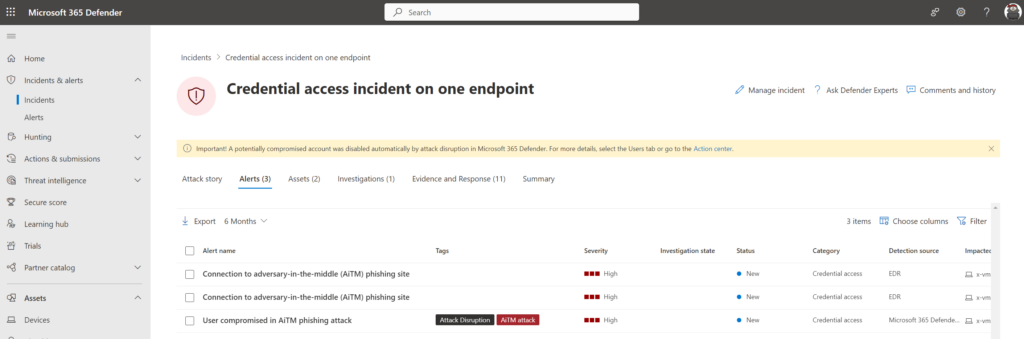
Adversary-in-the-middle phishing attacks are still more common in use. Since the removal of basic authentication from Exchange Online more and more attackers are using more modern attacks like adversary-in-the-middle phishing, cookie theft, and other used attacks. Last year I blogged about several modern

From cookie theft to BEC: Attackers use AiTM phishing sites as entry point to further financial fraud

Advanced BEC Scam Campaign Targeting Executives on O365

Microsoft: Phishing bypassed MFA in attacks against 10,000 orgs

Microsoft Details Phishing Campaign Targeting Over 10,000 Organizations
AiTM/ MFA phishing attacks in combination with new Microsoft protections (2023 edition)

Has MFA Failed Us? How Authentication Is Only One Part of the Solution - SentinelOne

Hackers use AiTM attack to monitor Microsoft 365 accounts for BEC scams

Microsoft Defender Weekly Wrap - Issue #83 - by Rod Trent

What Is An Adversary-in-The-Middle Attack (AiTM)?

Jeffrey Appel on LinkedIn: How to protect Azure storage accounts (Blob) using Defender for Storage
de
por adulto (o preço varia de acordo com o tamanho do grupo)






