Major surge in memory-based attacks as hackers evade traditional
Por um escritor misterioso
Descrição
Protecting workloads with tools that understand how to interpret attacks on cloud runtime environments is crucial.

115 cybersecurity statistics + trends to know in 2024

Machine learning and blockchain technologies for cybersecurity in

Bloomberg Crypto Channel Hack Exposes Discord Users to Phishing

Three flaws allow attackers to bypass UEFI Secure Boot feature

10 Malware Examples and 6 World Famous Attacks
“PACMAN” Hack Breaks Apple M1's Last Line of Defense - IEEE

Has an AI Cyber Attack Happened Yet?
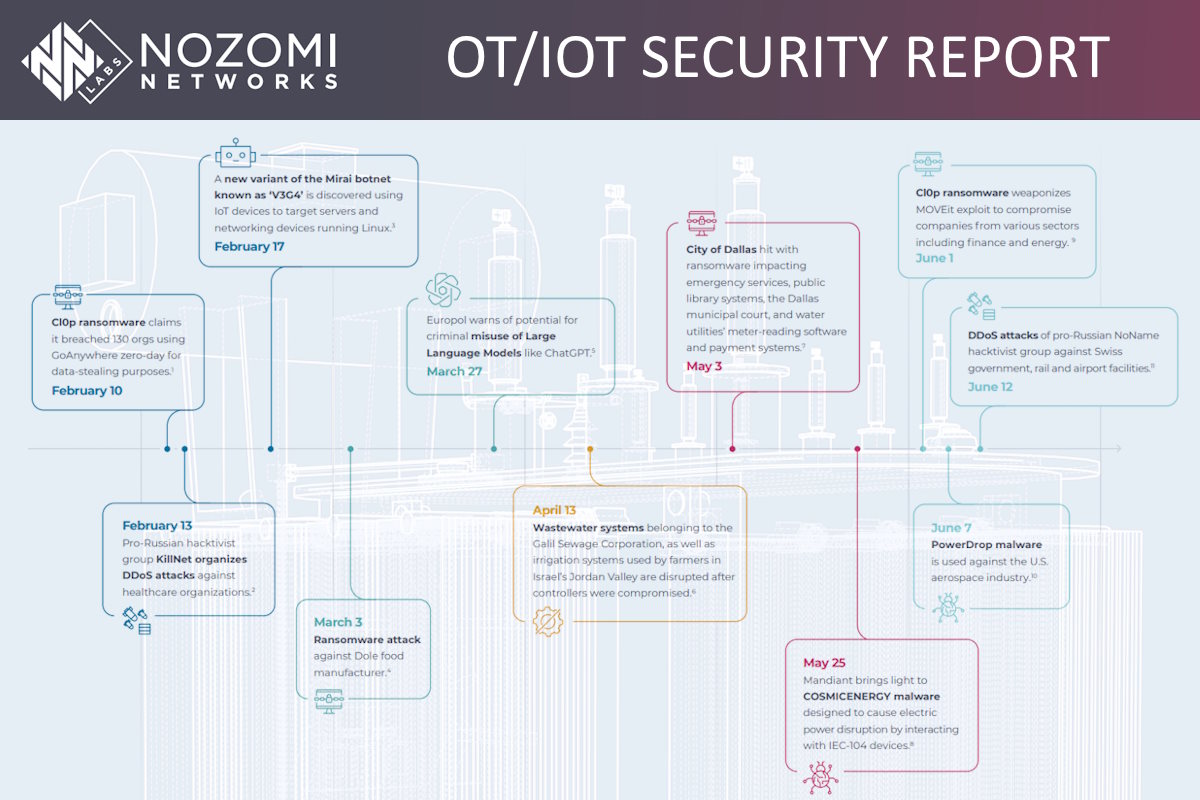
Malware activity surges, threatening OT and IoT environments with

Complete Guide to Ransomware: How to Recover and Prevent an Attack

CYFIRMA QUARTERLY RANSOMWARE REPORT : Q3 2023 - CYFIRMA
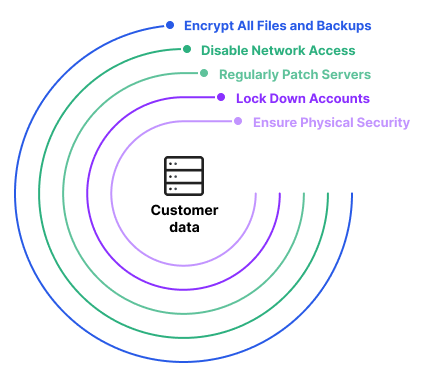
What is Database Security, Threats & Best Practices

Memory-Based Cyberattacks Become More Complex, Difficult To Detect

Security 101: The Rise of Fileless Threats that Abuse PowerShell
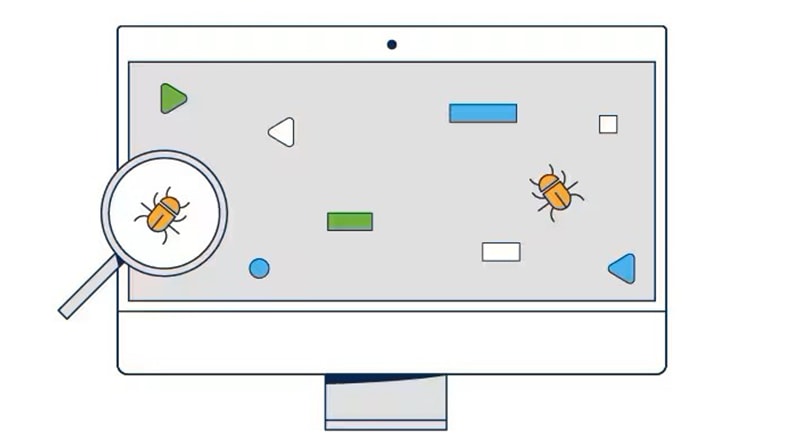
What Is Malware? - Definition and Examples - Cisco

What is a Fileless Malware Attack (with examples)
de
por adulto (o preço varia de acordo com o tamanho do grupo)

_new-roblox-evade-script-hack-gui-124-auto-farm-124-god-mode-124-infinite-money-amp-more-pastebin-2022-preview-hqdefault.jpg)