Initial access broker repurposing techniques in targeted attacks
Por um escritor misterioso
Descrição
Describing activities of a crime group attacking Ukraine.
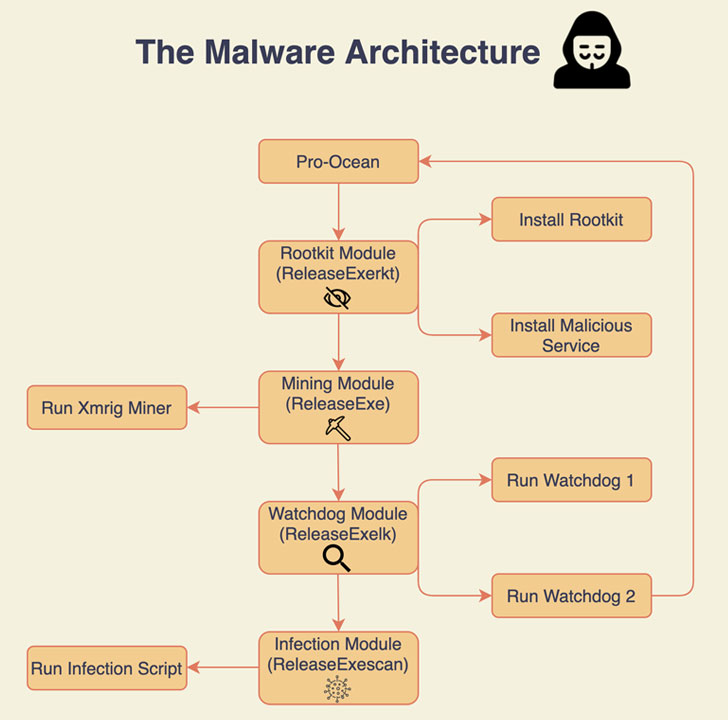
New Cryptojacking Malware Targeting Apache, Oracle, Redis Se - vulnerability database
6 Types of Database Hacks Use to Obtain Unauthorized Access

Cisco Umbrella discovers evolving cyberthreats in first half of 2020

Threat Trends: DNS Security, Part 1 - Storcom, Lombard, Illinois, United States of America

Scraping-as-a-Service: How a Harmless Tool Became a Cyber Threat
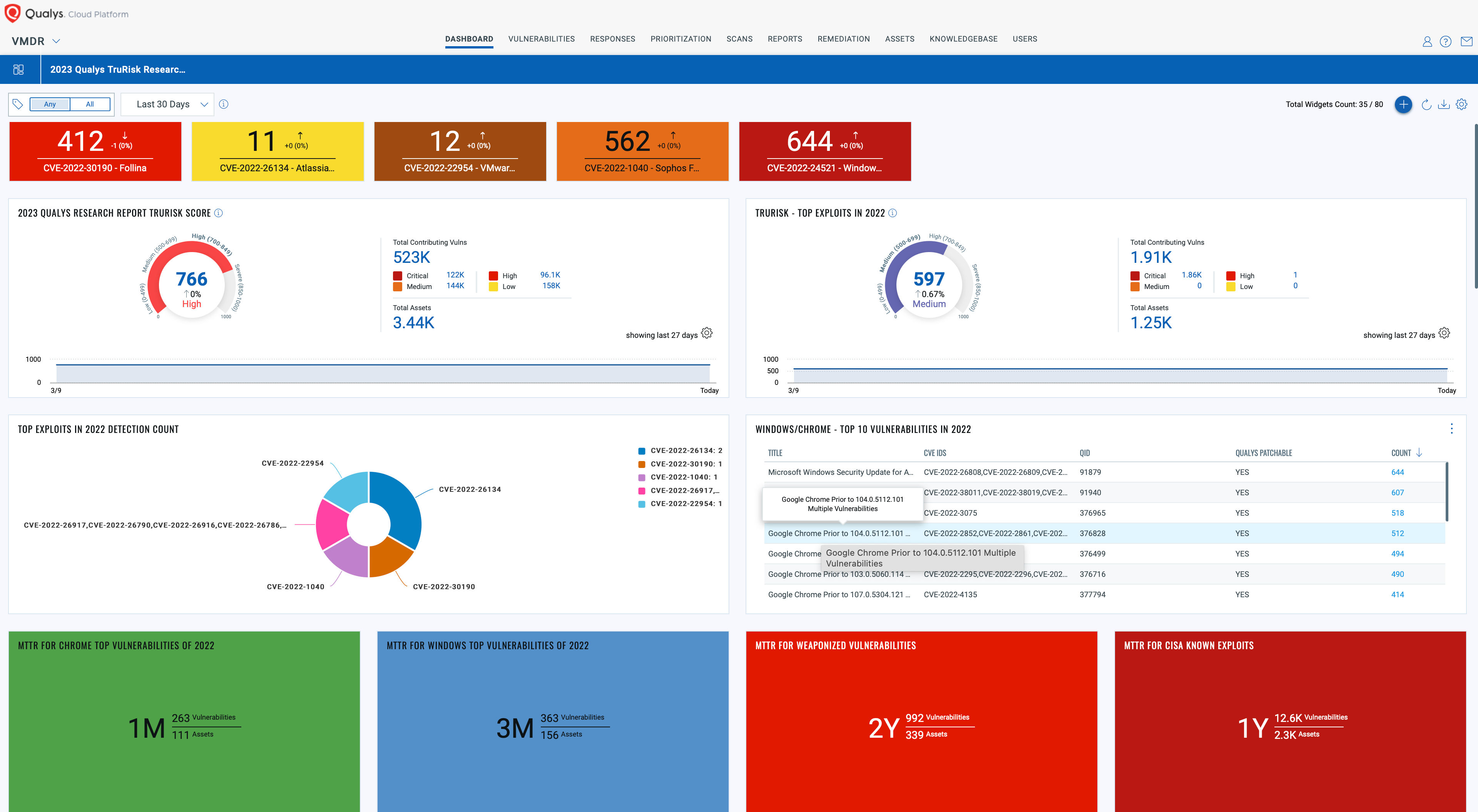
Cybersecurity Risk Fact #3: Initial Access Brokers Attack What Organizations Ignore

Initial access brokers: How are IABs related to the rise in ransomware attacks?

Scraping-as-a-Service: How a Harmless Tool Became a Cyber Threat
Cybersecurity Risk Fact #3: Initial Access Brokers Attack What Organizations Ignore

Transfer Learning: Repurposing ML Algorithms from Different Domains to Cloud Defense
de
por adulto (o preço varia de acordo com o tamanho do grupo)